Table of Contents
The DCRat malware campaign is targeting hotel staff across Europe using fake Booking.com emails and a bogus Blue Screen of Death to deliver a .NET remote access trojan. Tracked by Securonix as PHALT#BLYX, the operation uses ClickFix-style prompts to coerce victims into running a PowerShell command.
Attackers send fake booking.com phishing emails about reservation cancellations that redirect to a spoofed Booking.com page with a CAPTCHA, then a fake BSoD that instructs users to paste a command into Run.
That command fetches and launches DCRat via MSBuild, alters Microsoft Defender settings to evade detection, and persists on the host. The activity began in late December 2025.
DCRat malware campaign: What You Need to Know
- The DCRat malware campaign uses fake Booking.com emails, a BSoD decoy, and MSBuild to deliver a .NET RAT that evades Defender and targets hotel staff.
- Bitdefender – Endpoint protection with strong ransomware and exploit defense.
- 1Password – Enterprise-grade password manager with phishing-resistant sharing.
- Passpack – Team credential vault to reduce password reuse risk.
- EasyDMARC – Stop spoofing and strengthen email authentication.
- IDrive – Secure backups to mitigate malware impact and data loss.
- Tenable Vulnerability Management – Find and fix exposed assets attackers target.
- Auvik – Network visibility to spot suspicious lateral movement.
How the Phishing Works
The DCRat malware campaign begins with brand impersonation. Attackers send fake booking.com phishing emails claiming a reservation was cancelled, pushing staff to verify via a link.
Messages include room charge details in Euros, indicating a European focus. For broader context on brand abuse, see brand impersonation phishing scams, and additional awareness resources on phishing risks and safety.
From fake booking.com phishing emails to a bogus BSoD
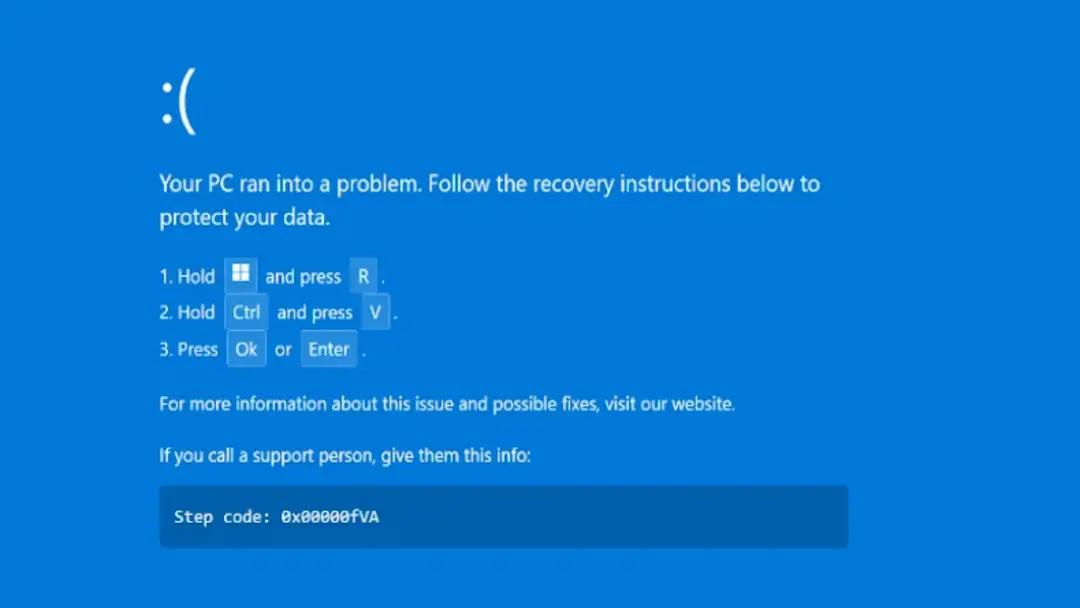
Victims are sent to a counterfeit site (e.g., low-house[.]com) that imitates Booking.com and displays a fake CAPTCHA. After passing it, the site shows a fake BSoD page with scripted “recovery instructions.”
The page directs users to open Windows Run, paste a command, and press Enter, initiating the DCRat malware campaign payload chain.
ClickFix-style instructions drive execution
This mirrors ClickFix BSoD malware attacks: tightly scripted prompts that cause users to execute the command themselves. In the DCRat malware campaign, that single action launches a PowerShell dropper that retrieves code silently.
Related social engineering patterns, including voice-based lures, are covered in vishing attack guidance.
Inside the DCRat Payload
Once executed, the DCRat malware campaign advances through multiple stages to establish control, evade detection, and maintain persistence on Windows hosts.
Living-off-the-land via MSBuild.exe
The PowerShell dropper downloads an MSBuild project (v.proj) from 2fa-bns[.]com and runs it with MSBuild.exe.
This living-off-the-land technique helps the DCRat malware campaign blend with legitimate processes and bypass simplistic detections.
Defender evasion, persistence, and UAC abuse
The embedded payload modifies Microsoft Defender Antivirus exclusions, adds persistence via the Startup folder, and retrieves the RAT from the same domain. With admin rights, it may disable Defender entirely.
Without elevation, it loops a UAC prompt every two seconds (three times) to encourage privilege approval. To distract users, it opens the legitimate Booking.com admin page, maintaining the illusion of normal activity throughout the DCRat malware campaign.
For foundational threat awareness, review this malware overview.
What DCRat can do
DCRat (DarkCrystal RAT, a variant of AsyncRAT) is an off-the-shelf .NET backdoor. In the DCRat malware campaign, once the RAT checks in, operators can profile the host, log keystrokes, execute commands, and deliver additional payloads, including cryptocurrency miners.
The plugin-based design supports rapid capability expansion. For perspective on credential risks, see how AI can crack your passwords.
Attribution Clues and Targeting
The DCRat malware campaign consistently targets European hospitality organizations. Lures impersonate Booking.com and include Euro-denominated charges.
Securonix observed Russian-language strings inside the v.proj file, aligning with Russian-speaking actors known to use DCRat, though no specific group is attributed.
Practical Steps for Defenders
Because the DCRat malware campaign abuses trusted binaries like MSBuild.exe, defenders should restrict script execution and monitor suspicious parent-child process chains.
Watch for Defender exclusion tampering, repeated UAC prompts, and outbound connections after sessions on booking-themed sites. Train staff to validate cancellation notices in official dashboards rather than email links.
See practical tips on how to avoid phishing attacks and reinforce detection-focused operations through weekly threat insights.
Implications for the Hospitality Sector and Beyond
The DCRat malware campaign demonstrates how living-off-the-land techniques reduce attacker costs and complicate defense.
By leveraging PowerShell and MSBuild, adversaries avoid noisy binaries and sidestep basic endpoint policies, enabling scalable, low-friction footholds.
Operationally, the DCRat malware campaign underscores the limits of signature-heavy controls and the need for behavioral analytics. Monitoring Defender tampering, MSBuild abuse, and anomalous UAC prompting can expose intrusions.
Security awareness for frontline staff remains crucial against convincing booking-themed lures and ClickFix BSoD malware attacks.
- Tresorit – Encrypted cloud storage to secure reservation documents and IDs.
- Optery – Remove exposed staff data to reduce targeted phishing risk.
- Tenable Exposure Management – Map attack paths across IT assets.
- IDrive – Immutable backups to speed recovery after malware incidents.
- EasyDMARC – Enforce DMARC, DKIM, SPF to thwart domain spoofing.
- 1Password – Phishing-resistant passkeys and access controls for staff.
- Auvik – Detect rogue devices and unusual lateral movement on hotel networks.
Conclusion
The DCRat malware campaign blends social engineering with trusted Windows tools to bypass defenses in European hotels. A single Run command from a fake BSoD triggers a multi-stage compromise.
By mixing MSBuild execution, Defender exclusion changes, and distraction with legitimate Booking.com pages, operators secure persistence and control while masking malicious activity.
Organizations should harden PowerShell and MSBuild use, audit Defender configuration changes, and train staff to distrust urgent cancellation emails. The DCRat malware campaign illustrates how one click can escalate to full compromise.
Questions Worth Answering
What payload does the campaign deliver?
- DCRat (DarkCrystal RAT), a .NET backdoor for command execution, keylogging, and secondary payload delivery.
How do attackers coerce execution?
- They use fake booking.com phishing emails and a ClickFix-style BSoD page that instructs users to paste a command into Run.
Which living-off-the-land tools are abused?
- PowerShell and MSBuild.exe are used to fetch, compile, and execute payloads while mimicking legitimate activity.
How does it bypass Microsoft Defender?
- It sets Defender exclusions, adds Startup persistence, attempts full disablement with admin rights, and spams UAC prompts to gain elevation.
Who is being targeted?
- European hospitality organizations, especially hotel staff managing reservations through Booking.com workflows.
When did activity begin?
- Late December 2025, tracked by Securonix as PHALT#BLYX.
What mitigations help?
- Constrain PowerShell/MSBuild, monitor Defender tampering and UAC anomalies, and verify cancellations within official portals.
About Securonix
Securonix is a cybersecurity company focused on research and threat detection for enterprise environments. Its team examines emerging campaigns and adversary tradecraft.
In this case, Securonix analyzed PHALT#BLYX and detailed how the DCRat malware campaign abuses MSBuild, PowerShell, and social engineering for access.
The reporting outlines practical detection points, including Defender exclusion tampering and process lineage anomalies, to help reduce risk across organizations.
- Tresorit for Teams – Secure collaboration for distributed hotel staff.
- Optery – Reduce targeted spear-phishing by removing exposed PII.
- Bitdefender – Robust EDR to detect MSBuild and PowerShell abuse.
- Tenable – Prioritize vulnerabilities exploitable in current campaigns.
- EasyDMARC – Stop booking-themed spoofing at the mail gateway.
- IDrive – Rapid rollback after malware incidents and data loss.
- Auvik – Continuous network monitoring across hotel sites.