Table of Contents
Chrome extensions stealing ChatGPT were discovered on the Chrome Web Store, silently exfiltrating private AI conversations and browsing data to attacker-controlled servers.
Two lookalike AI sidebar extensions amassed 900,000 installs while exporting ChatGPT and DeepSeek chats and open tab URLs every 30 minutes.
Researchers describe the tactic as Prompt Poaching and warn it mirrors broader browser extension data collection trends, including in some mainstream add-ons.
Chrome extensions stealing ChatGPT: What You Need to Know
- Two AI sidebars with 900k installs exfiltrate AI chats and tab URLs every 30 minutes while impersonating a legitimate AITOPIA tool.
Recommended defenses and privacy tools
- Endpoint protection: Bitdefender blocks malware and malicious Chrome extensions 2026 variants.
- Password security: 1Password reduces credential theft risk from browser extension data theft.
- Encrypted cloud storage: Tresorit protects sensitive files synced from the browser.
- Personal data removal: Optery removes exposed personal info targeted by spyware operators.
What was discovered
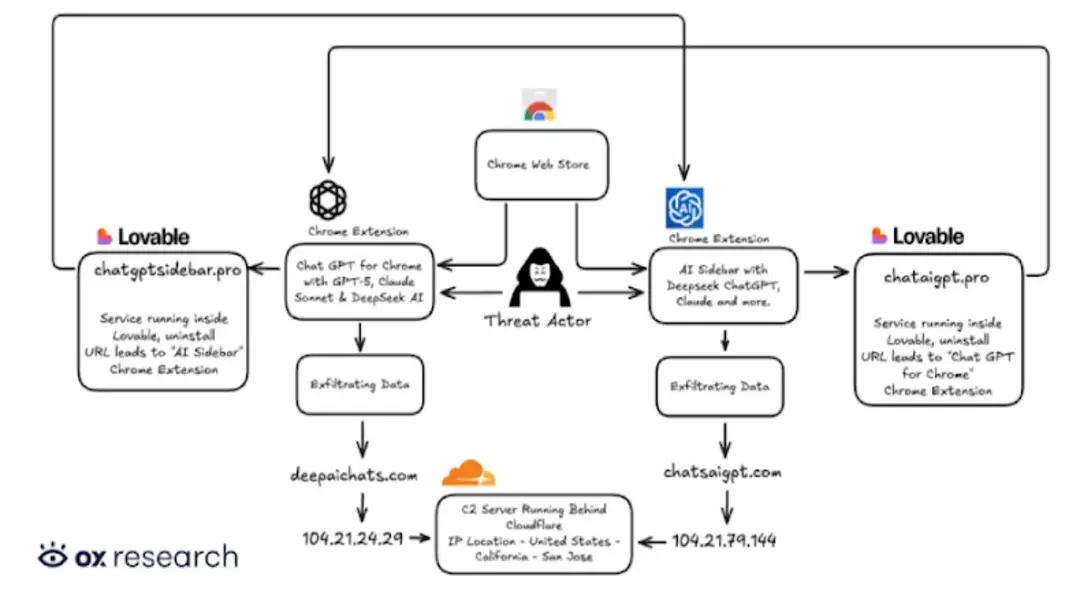
Our analysis confirms that two lookalike AI sidebars, effectively Chrome extensions that steal ChatGPT and DeepSeek conversations, were installed by more than 900,000 users.
The extensions are “Chat GPT for Chrome with GPT-5, Claude Sonnet & DeepSeek AI” (ID: fnmihdojmnkclgjpcoonokmkhjpjechg) and “AI Sidebar with Deepseek, ChatGPT, Claude, and more.” (ID: inhcgfpbfdjbjogdfjbclgolkmhnooop).
Both presented as productivity tools but operated as spyware, harvesting AI chats and tab activity every 30 minutes. As of publication, both remain listed on the Chrome Web Store; one lost its Featured badge.
The two extensions
These Chrome extensions stealing ChatGPT were observed at scale:
- Chat GPT for Chrome with GPT-5, Claude Sonnet & DeepSeek AI, approximately 600,000 users
- AI Sidebar with Deepseek, ChatGPT, Claude, and more. Approximately 300,000 users
How the data theft works
Once installed, the add-ons request consent for anonymous analytics, then act as Chrome extensions stealing ChatGPT history.
They scrape page elements (DOM), cache complete ChatGPT and DeepSeek conversations locally, and exfiltrate data to a remote command-and-control server.
This behavior aligns with infostealer tradecraft. For background on infostealers and collection mechanisms, see our guide to understanding infostealer malware.
Exfiltration targets and cadence
The extensions transmitted data roughly every 30 minutes to attacker infrastructure, including chatsaigpt[.]com and deepaichats[.]com. Beyond AI chats, they captured all open Chrome tab URLs.
Operators leveraged Lovable to host obfuscating assets, privacy policies, and telemetry pages at chataigpt[.]pro and chatgptsidebar[.]pro.
Impersonation and infrastructure
The pair impersonated AITOPIA’s legitimate “Chat with all AI models (Gemini, Claude, DeepSeek…) & AI Agents,” demonstrating how Chrome extensions stealing ChatGPT piggyback on trusted branding to accelerate adoption.
Their infrastructure blended malicious telemetry with benign-looking policy sites to avoid scrutiny.
Prompt Poaching moves mainstream
Secure Annex refers to this technique as Prompt Poaching, previously seen with Urban VPN Proxy. The core risk, the covert capture of AI prompts and outputs, now extends beyond clearly malicious Chrome extensions in 2026 to legitimate analytics and productivity tools.
Similarweb and Stayfocusd
Secure Annex reports that Similarweb and Sensor Tower’s Stayfocusd exhibit prompt collection behaviors.
Similarweb introduced conversation monitoring in May 2025 and, on January 1, 2026, updated terms to state it collects inputs, outputs, and attachments from AI tools for traffic and engagement analysis.
A December 30, 2025 policy update acknowledged possible processing of sensitive data.
Analysis indicates Similarweb collects conversation data via DOM scraping or by intercepting browser APIs such as fetch() and XMLHttpRequest(), loading remote parsing logic for ChatGPT, Anthropic Claude, Google Gemini, and Perplexity.
Researchers observed this across Chrome and Edge; its Firefox add-on was last updated in 2019. These methods mirror the risk model raised by Chrome extensions stealing ChatGPT content.
Policy and monetisation concerns
Researchers question whether dynamic behaviors in some add-ons align with Google’s single‑purpose extension rules and prohibitions on dynamically loaded code.
They also warn more developers may adopt similar libraries to monetize usage analytics, blurring boundaries between helpful features and browser extension data theft.
For broader context on extension risks and patching cadence, review our prior coverage of compromised Chrome extensions and the Chrome stable channel security update. Also see our analysis of an exploited Chrome zero‑day and prompt injection risks.
Security and privacy implications for users and organizations
Legitimate extensions can enhance productivity, centralize access to models, and deliver analytics. Teams often rely on AI sidebars to streamline research and drafting workflows.
The downside is immediate and severe. Chrome extensions stealing ChatGPT can expose corporate intellectual property, personal identifiers, and internal URLs, fuel for espionage, identity theft, and targeted phishing.
Organizations whose users installed these add-ons may have leaked confidential business and customer data, a clear case of browser extension data theft.
Harden your browser stack
- Network visibility: Auvik monitors outbound connections to suspicious domains.
- Vulnerability detection: Tenable identifies risky extensions and exposed assets.
- DMARC protection: EasyDMARC reduces phishing fallout from stolen data.
- Secure backups: IDrive safeguards endpoints impacted by spyware or account takeover.
Conclusion
Uninstall any Chrome extensions stealing ChatGPT and revoke site access and data permissions immediately.
Featured badges are not a guarantee of safety. Favor reputable publishers, audit requested permissions, and avoid unknown AI sidebars.
Until platforms curb malicious Chrome extensions 2026, enforce least privilege, monitor outbound traffic, and run regular extension audits to limit browser extension data theft.
Questions Worth Answering
Which extensions are involved?
– “Chat GPT for Chrome with GPT-5, Claude Sonnet & DeepSeek AI” and “AI Sidebar with Deepseek, ChatGPT, Claude, and more.” were flagged.
What data was taken?
– Full ChatGPT and DeepSeek conversations plus all open Chrome tab URLs were exfiltrated to attacker-controlled servers.
Are the extensions still available?
– Both remain listed on the Chrome Web Store at publication time; one lost its Featured badge.
Are Similarweb or Stayfocusd malicious?
– They are not categorized as Chrome extensions stealing ChatGPT, but researchers say they collect AI inputs under their stated policies.
How can users reduce risk?
– Remove suspicious add-ons, limit site access, audit permissions, and deploy endpoint protection and DNS monitoring.
Does this affect Edge or Firefox?
– Similarweb’s prompt collection was observed on Chrome and Edge; its Firefox add-on hasn’t been updated since 2019.
About OX Security
OX Security is a cybersecurity firm focused on risks across software supply chains, cloud environments, and endpoints. Its research covers active threats and emerging techniques.
The team analyzed the malicious extensions that exfiltrated AI conversations and browser activity on a timed schedule, exposing privacy and IP risks.
OX Security publishes findings to help organizations reduce risk and strengthen browser, application, and cloud security posture.
About Moshe Siman Tov Bustan
Moshe Siman Tov Bustan is a researcher at OX Security specializing in modern malware techniques and browser-based threats.
He detailed how the extensions scraped DOM elements and exported ChatGPT data every 30 minutes to attacker infrastructure.
His work highlights rising risks at the intersection of browser security, AI adoption, and enterprise data protection.
Explore more security essentials: Passpack, Tenable solutions, and CyberUpgrade training to harden your environment.