Table of Contents
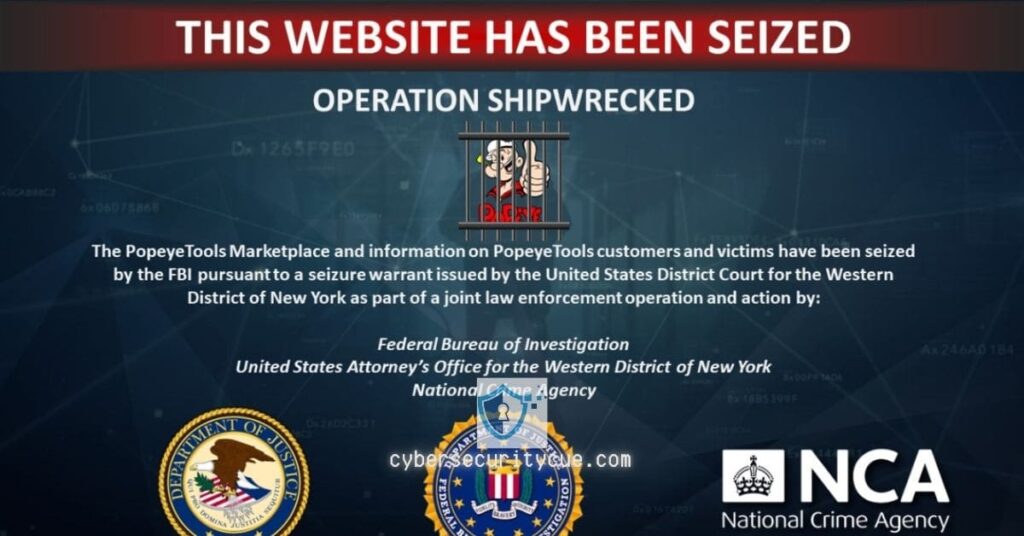
Recently, we read about the PopeyeTools takedown, which marked a critical turning point in the fight against cybercrime, and in the same vain a blow to the administrators and users of that platform. This dark web marketplace, which once thrived by trading stolen credit card information and personal data, was been shut down by the U.S. Department of Justice (DOJ).
For years, PopeyeTools facilitated financial fraud, offering tools and services that empowered cybercriminals worldwide. Its closure sends a strong message, but it also raises important questions about the broader fight against cybercrime and the evolving threats we face.
The effects of PopeyeTools Takedown go beyond headlines. While it disrupts one of the largest hubs for illicit online activity, it also challenges us to prepare for what might come next.
Are we equipped to tackle other platforms that might rise to take its place?
Key Takeaway to PopeyeTools Takedown:
- PopeyeTools Takedown: The PopeyeTools takedown is a victory for cybersecurity, but staying vigilant against future threats is essential.
Overview of the key details about PopeyeTools and the reasons it was taken down:
| Aspect | Details |
|---|---|
| Name | PopeyeTools |
| Type of Platform | Online marketplace for stolen credit card information and personal data |
| Launch Year | Around 2016 |
| Primary Activities | – Selling stolen bank account, credit card, and debit card details – Providing tools to validate stolen data – Offering refunds or replacements for invalid goods |
| Number of Users | Thousands of users worldwide, including individuals linked to ransomware attacks |
| Revenue Generated | Over $1.7 million from selling stolen data and fraud-related services |
| Data Impacted | Personally identifiable information (PII) of more than 227,000 individuals |
| Key Features | – Validation tools to check stolen data usability – Refund policies for invalid purchases – Immediate usability of sold data |
| Reason for Shutdown | Facilitating cybercrime and fraud on a massive scale, enabling financial fraud globally |
| Domains Seized | – PopeyeTools.com – PopeyeTools.co.uk – PopeyeTools.to |
| Administrators Charged | – Abdul Ghaffar (25, Pakistan) – Abdul Sami (35, Pakistan) – Javed Mirza (37, Afghanistan) |
| Cryptocurrency Seized | Approximately $283,000 from Abdul Sami’s account |
| Danger to Society | – Enabled financial fraud through stolen credit card and bank account data – Provided easy-to-use tools for validating stolen data |
| Notable Similar Cases | Comparable to the takedown of AlphaBay, another major dark web marketplace dealing in illicit goods and data |
| Impact of Takedown | Disruption of a major hub for cybercrime, protecting individuals from financial fraud, and reducing the resources available to cyber criminals |
The Takedown: A Victory for Justice
The PopeyeTools takedown was part of a broader effort by the DOJ to crack down on cybercrime. United States authorities seized the platform’s domains, effectively shutting down access to the site.
Additionally, charges were filed against three administrators:
The DOJ also confiscated $283,000 in cryptocurrency linked to the platform. By targeting the platform and its operators, law enforcement delivered a significant blow to the cybercrime ecosystem.
Impact of PopeyeTools on Individuals and Businesses
The effects of PopeyeTools were devastating. Individuals and businesses worldwide suffered from financial fraud, identity theft, and data breaches orchestrated through the platform.
How PopeyeTools Affected Victims:
| Victim Type | Impact |
|---|---|
| Individuals | Loss of funds due to fraudulent transactions and identity theft. |
| Businesses | Data breaches, leading to financial losses, legal liabilities, and damaged reputations. |
| Financial Institutions | Increased costs for fraud detection, prevention, and reimbursement. |
The platform’s tools also enabled users to test stolen data, making fraud even more efficient. For example, PopeyeTools users could verify if a stolen credit card was still active, ensuring successful fraudulent transactions.
The Rise of Dark Web Marketplaces
What Are Dark Web Marketplaces?
Dark web marketplaces are hidden online platforms where users trade goods and services, often illicit in nature. These marketplaces operate on the dark web, a part of the internet not accessible through regular search engines or browsers.
To access them, users need special tools like Tor or I2P, which anonymize their activity and shield their identities.
With the dark web, anonymity is everything. It allows sellers and buyers to operate in secrecy, making these platforms a hub for illegal activities like the sale of stolen data, narcotics, counterfeit documents, and hacking tools.
For instance, PopeyeTools was one such marketplace, infamous for trading stolen credit card information and tools for fraud. The PopeyeTools Takedown revealed how much damage these platforms can cause, as thousands of users exploited stolen data to commit financial crimes worldwide.
How Dark Web Marketplaces Facilitate Cybercrime

Dark web marketplaces are crucial enablers of cybercrime. They provide a platform where malicious actors can buy and sell everything needed to carry out attacks.
Here’s a breakdown of how these marketplaces facilitate crime:
| Service or Product | How It Supports Cybercrime |
|---|---|
| Stolen Data | Offers stolen credit card details, Social Security numbers, and other PII for fraudulent use. |
| Hacking Tools | Provides malware, ransomware kits, and other software to attack systems. |
| Validation Services | Allows buyers to verify if stolen information, like credit cards, is still active. |
| Anonymity Tools | Sells tools like VPNs and cryptocurrency mixers to help criminals hide their tracks. |
Real-life example: When platforms like PopeyeTools thrive, they become a one-stop shop for criminals. Users could purchase stolen data, validate it using on-site tools, and execute fraud, all within one platform.
The Evolution of Dark Web Marketplaces
Dark web marketplaces didn’t always exist in their current sophisticated form. Let’s take a brief look at their evolution:
| Era | Description |
|---|---|
| Early Days | Simple forums and chat rooms where users manually shared illicit goods and services. |
| Marketplaces Emerge | Platforms like Silk Road introduced organized marketplaces with payment systems and customer reviews. |
| Advanced Platforms | Sites like PopeyeTools used modern technology, offering advanced features like refunds and data validation. |
Over time, these platforms have become more professional, with features designed to attract users and build trust, despite their illegal nature.
PopeyeTools, for example, offered a refund policy for invalid stolen data, mimicking the customer-first approach of legitimate e-commerce platforms.
This evolution demonstrates how adaptable cybercriminals are. When law enforcement shuts down one marketplace, another often rises to take its place, sometimes with even more advanced capabilities.
The rise and eventual PopeyeTools takedown show the significant role dark web marketplaces play in modern cybercrime.
While taking down platforms like PopeyeTools is a critical victory, understanding their history and operations helps us better prepare for what may come next.
The Impact of PopeyeTools
The PopeyeTools takedown was a major victory in the fight against cybercrime, but its effects have revealed the serious damage caused by this dark web marketplace. From stolen data to ruined reputations, the platform left a trail of harm in its wake.
Let’s take a closer look at how PopeyeTools impacted individuals and businesses, and what the broader implications of this dark web operation were.
How PopeyeTools Affected Individuals and Businesses
PopeyeTools wasn’t just another dark web marketplace, but a hub for trading stolen information that directly impacted lives and livelihoods.
Individuals
For individuals, PopeyeTools facilitated the theft of personal information such as Social Security numbers, credit card details, and online account credentials. This stolen data was then used to:
- Drain bank accounts
- Make unauthorized purchases
- Commit identity theft
Real-life example: Imagine waking up to find your credit card maxed out because someone used your details to buy expensive electronics. Victims of PopeyeTools often faced such situations, leading to months, or even years, of financial recovery and stress.
Businesses
For businesses, PopeyeTools was a nightmare. Criminals purchased data to launch targeted phishing attacks, ransomware campaigns, and other malicious activities. This not only caused financial losses but also eroded trust with customers.
Key impacts on businesses:
- Data Breaches: Sensitive customer data was leaked and sold.
- Financial Losses: Businesses faced lawsuits and hefty fines for inadequate cybersecurity measures.
- Reputational Damage: Customers lost confidence in brands that couldn’t protect their data.
Types of Data Stolen and Sold on PopeyeTools
PopeyeTools offered a smorgasbord of stolen data, making it a goldmine for cybercriminals. Here’s a breakdown of the types of data traded on the platform:
| Type of Data | Usage in Cybercrime |
|---|---|
| Credit Card Information | Used for unauthorized purchases or to clone cards. |
| Bank Account Details | Allowed criminals to make fraudulent transfers or withdrawals. |
| Personally Identifiable Information (PII) | Enabled identity theft and account takeovers. |
| Login Credentials | Facilitated phishing scams and hacking into personal or business accounts. |
| Corporate Data | Used to launch ransomware attacks or blackmail companies for financial gain. |
By offering validation tools, PopeyeTools made it easy for buyers to ensure that stolen data was still active and ready for fraudulent use. This feature alone increased the platform’s appeal to criminals worldwide.
Financial and Reputational Damage from PopeyeTools
The effects of PopeyeTools takedown revealed the true scale of the platform’s impact. Data breaches linked to the marketplace caused severe financial and reputational harm to victims.
Financial Losses
For individuals, stolen data often resulted in drained accounts and ruined credit scores. For businesses, the costs went beyond financial penalties, including:
- Data recovery expenses
- Increased cybersecurity investments
- Loss of revenue due to damaged customer trust
Real-life example: In one case, a small business faced a ransomware attack traced back to stolen credentials sold on PopeyeTools. The attack cost the company $200,000 in recovery efforts and legal fees.
Reputational Damage
Reputation is everything in today’s digital world. For companies, being associated with a data breach often leads to:
- Public backlash
- Negative press
- Loss of loyal customers
Statistics show that nearly 70% of customers would stop doing business with a company that suffered a major data breach. PopeyeTools amplified this risk by making sensitive data easily accessible to bad actors.
The effects of PopeyeTools Takedown are a sobering reminder of how much damage dark web marketplaces can inflict. The platform’s operation highlights the urgent need for stronger cybersecurity measures and international collaboration to combat such threats. By understanding these impacts, we can better protect ourselves and prepare for the next challenge.
The Takedown and Its Implications
The PopeyeTools takedown marked a significant step forward in the fight against cybercrime. Spearheaded by the US Department of Justice (DOJ), the operation not only disrupted a major dark web marketplace but also showed the ongoing battle between law enforcement and cyber criminals.
Here’s how it all went down and what it means for the future of cybersecurity.
Actions Taken by the US Department of Justice

To dismantle PopeyeTools, the DOJ executed a well-coordinated plan that targeted both the platform and its administrators. This included:
- Seizing Domains: Authorities legally seized PopeyeTools’ primary web domains (.com, .co.uk, and .to), effectively cutting off user access to the platform.
- Arresting Key Figures: Charges were filed against Abdul Ghaffar, Abdul Sami, and Javed Mirza, alleged administrators of PopeyeTools. These individuals operated from Pakistan and Afghanistan, underscoring the international nature of cybercrime.
- Confiscating Assets: The DOJ seized $283,000 in cryptocurrency linked to PopeyeTools. These funds were proceeds from selling stolen data, highlighting the platform’s financial success at the expense of its victims.
Table: Key DOJ Actions
| Action | Details |
|---|---|
| Domain Seizure | Shut down .com, .co.uk, and .to domains. |
| Arrests | Charged three administrators in Pakistan and Afghanistan. |
| Asset Seizure | Confiscated $283,000 in cryptocurrency. |
These measures collectively disrupted PopeyeTools and sent a strong message to other dark web operators.
Legal and Technical Challenges
Taking down platforms like PopeyeTools isn’t easy. It involves a mix of legal expertise, international cooperation, and cutting-edge technical skills.
Legal Challenges
- Jurisdiction Issues: PopeyeTools operated internationally, with administrators based in different countries. This required extensive collaboration between US authorities and foreign governments.
- Evidentiary Requirements: Collecting enough evidence to prosecute the administrators without alerting them was a meticulous process.
Technical Challenges
- Anonymity on the Dark Web: PopeyeTools operated on the dark web, using encrypted connections to hide its location and users. This made tracking the platform extremely difficult.
- Blockchain Complexity: Tracking cryptocurrency transactions required advanced blockchain analysis tools to link digital wallets to criminal activity.
Despite these challenges, the successful PopeyeTools Takedown demonstrated the DOJ’s growing capability to tackle cybercrime.
Short-Term and Long-Term Implications
The effects of PopeyeTools Takedown are already being felt in the cybercrime landscape.
Short-Term Impacts
- Disruption of Operations:
With PopeyeTools gone, thousands of cybercriminals lost access to stolen data and validation services. This caused a temporary setback for their illegal activities. - Increased Awareness:
The takedown received significant media coverage, alerting individuals and businesses to the risks of data breaches and the importance of online security.
Long-Term Impacts
- Deterrence Effect
The arrests and asset seizures serve as a warning to other dark web operators. They show that even anonymized platforms can be taken down with the right resources and determination. - Evolving Cybercrime Tactics
Cybercriminals will likely adapt to avoid detection, developing more sophisticated platforms and methods. This shows the need for ongoing vigilance and innovation in cybersecurity.
The PopeyeTools takedown was a landmark achievement, but it also highlights the challenges ahead. While the immediate disruption of a major dark web marketplace is a victory, the long-term fight against cybercrime is far from over.
We must remain proactive, investing in advanced cybersecurity measures and fostering international collaboration to address this ever-evolving threat.
The road ahead may be complex, but every takedown brings us one step closer to a safer online world.
The Future of Cybercrime and Data Security
The PopeyeTools takedown has been hailed as a major victory in the fight against cybercrime, but it also raises a larger question: What’s next for cybercriminals, and how can we stay ahead of evolving threats?

The effects of PopeyeTools Takedown are far-reaching, but this operation is only one step in an ongoing battle to protect data and combat online threats.
As cybercrime continues to grow more sophisticated, we must consider how emerging technologies, better cybersecurity practices, and international cooperation can help protect individuals and organizations alike.
The Evolving Tactics of Cybercriminals
Cybercrime is constantly changing. While law enforcement may have dealt a blow to platforms like PopeyeTools, cybercriminals are not going away. Their tactics are evolving and becoming more complex, often making it harder for authorities to keep up.
- Anonymity and Encryption
One of the biggest challenges law enforcement faces in dealing with cybercrime is the anonymity provided by the dark web. Platforms like PopeyeTools relied on encryption, making it difficult for authorities to track transactions or even identify perpetrators. This is a common tactic used by cybercriminals to stay one step ahead. - Decentralized Platforms
Many criminals are now moving towards decentralized platforms, making them harder to target or shut down. Unlike PopeyeTools, which was a central marketplace, decentralized platforms don’t have a single point of failure, which makes them much harder to take down. - Increased Use of Ransomware
Cybercriminals are increasingly relying on ransomware as a way to extort money. By encrypting a victim’s data and demanding payment for its release, they can generate significant revenue. The rise of ransomware attacks shows how adaptable cybercriminals are, finding new ways to exploit vulnerabilities.
Table: Emerging Cybercrime Tactics
| Cybercrime Tactic | Impact on Law Enforcement |
|---|---|
| Anonymity via the Dark Web | Makes tracking cybercriminals more difficult. |
| Decentralized Platforms | Prevents easy shutdown of illegal marketplaces. |
| Ransomware Attacks | Forces victims into paying to regain access to data. |
The Role of Emerging Technologies in Combating Cybercrime
As cybercriminals grow more sophisticated, so too must our methods for combatting them. Emerging technologies like artificial intelligence (AI) and machine learning are playing a crucial role in identifying and preventing cybercrime.
- AI for Threat Detection
AI can analyze vast amounts of data and identify patterns that might be missed by human analysts. This makes it easier to detect cybercrime activity in real-time such as identifying unusual transactions on the dark web or spotting phishing attempts. - Machine Learning for Predictive Security
Machine learning can predict cyber threats before they happen by analyzing historical data. By recognizing trends in cyberattacks, organizations can proactively safeguard their systems, staying one step ahead of cybercriminals. - Blockchain for Transparency
Blockchain technology, often associated with cryptocurrencies, can provide a transparent and immutable ledger for transactions. This could be used to trace stolen data or illegal transactions back to their source, increasing accountability in the digital world.
Table: Emerging Technologies in Cybersecurity
| Can detect patterns and identify threats in real-time. | Impact on Cybersecurity |
|---|---|
| AI for Threat Detection | Can detect patterns and identify threats in real time. |
| Machine Learning | Predicts and prevents potential cyberattacks. |
| Blockchain | Increases transparency and traceability in digital transactions. |
The Importance of Strong Cybersecurity Practices
While technology plays a significant role in fighting cybercrime, individuals and organizations also need to take proactive steps to protect themselves.
- Education and Awareness
One of the easiest ways to prevent cybercrime is through education. Individuals must be aware of common scams, phishing attempts, and security best practices. For example, recognizing suspicious emails or avoiding public Wi-Fi networks can help prevent many cybercrimes from occurring. - Implementing Strong Passwords
Using strong, unique passwords for every account is crucial. Cybercriminals often rely on stolen credentials, and weak passwords are an easy target. Multi-factor authentication (MFA) adds “an additional” layer of protection, making it harder for attackers to gain unauthorized access. - Regular Software Updates
Outdated software is one of the most common entry points for cybercriminals. Organizations and individuals must regularly update their systems to patch security vulnerabilities. This simple step can prevent many data breaches. - Data Encryption
Encrypting sensitive data ensures that even if it is stolen, it remains unreadable without the encryption key. This is particularly important for businesses handling customer information.
The Need for International Cooperation
Cybercrime knows no borders, and as PopeyeTools’ takedown demonstrated, international cooperation is crucial in combating this global issue.
- Global Reach of Cybercriminals
Cybercriminals often operate across multiple countries, making it difficult for any one government to fully address the issue. By working together, nations can share intelligence, coordinate investigations, and execute joint operations to disrupt cybercrime networks. - Cross-Border Data Sharing
Laws and regulations vary from country to country, making it difficult to exchange information across borders. However, cooperation through organizations like INTERPOL, Afripol, and Europol is making it easier to track down criminals and dismantle global networks. - Unified Cybersecurity Standards
A unified approach to cybersecurity standards would help ensure that organizations worldwide are following best practices to protect their systems. This could include agreements on data protection laws and protocols for sharing threat intelligence.
The PopeyeTools takedown was a major success in the fight against cybercrime, but as we’ve seen, the battle is far from over. Cybercriminals are becoming more sophisticated, and technology is both helping and hindering the fight.

To stay ahead, we need to continue developing innovative solutions like AI, machine learning, and blockchain, while also strengthening our individual and organizational cybersecurity practices.
In the end, the future of cybercrime and data security will depend on ongoing collaboration, both within our borders and internationally. Only by working together can we hope to combat the ever-growing threat of cybercrime in our digital world.
Conclusion
The PopeyeTools takedown marks a significant step in the fight against cybercrime. In this article, we’ve explored the crucial aspects of the takedown, its impact on cyber criminals, and the broader implications for cybersecurity.
As we wrap up, let’s quickly revisit the key points we’ve discussed.
Key Points Recap
We’ve covered a lot, but here are the major takeaways:
- PopeyeTools was a key player in the dark web, providing cybercriminals with the tools and services they needed to conduct illicit activities like data breaches, hacking, and fraud.
- The PopeyeTools Takedown was a collaborative effort by law enforcement agencies, including the US Department of Justice, and it disrupted a major platform used by cybercriminals.
- The effects of PopeyeTools Takedown go beyond just taking down a website. It has sent a strong message that cybercrime is a priority for authorities, but it also underscores the ongoing need for vigilance against ever-evolving threats.
- The dark web remains a significant challenge, and while this takedown was a win, we must remain aware that cybercriminals are always adapting, using new tactics to stay one step ahead.
The Significance of the PopeyeTools Takedown
The PopeyeTools takedown is a major victory in the battle against cybercrime. This platform was one of the most well-known marketplaces for selling illegal hacking tools and stolen data. By dismantling it, authorities have severely disrupted many cybercriminal operations.
However, while this takedown is certainly a step in the right direction, it is only one part of the larger effort needed to combat cybercrime. We can take comfort in knowing that the justice system is actively tackling these platforms, but it’s essential to understand that this war is ongoing.
As we’ve discussed, cybercriminals will always find new ways to adapt. The effects of PopeyeTools Takedown are a reminder that law enforcement’s job is never done.
Continued Vigilance and Proactive Measures
As the PopeyeTools takedown proves, the landscape of cybercrime is constantly evolving, and staying ahead of these threats requires continuous effort. For individuals and organizations, it’s crucial to maintain strong cybersecurity practices.
- Be proactive: Make sure you are using updated security software, multi-factor authentication, and strong, unique passwords for all accounts.
- Stay informed: Cyber threats are constantly evolving, so keep yourself updated on the latest security trends and breach reports.
- Educate yourself and others: Phishing, ransomware, and data breaches are some of the most common ways cybercriminals strike. By learning about these attacks, you can better protect yourself and your organization.
We must all be proactive in securing our data and staying ahead of cybercriminals. The PopeyeTools takedown highlights the importance of cybersecurity in today’s world, but it also serves as a reminder that we can’t rely solely on law enforcement to protect us. Everyone has a role to play in this fight.
Call to Action: Stay Informed and Secure
The fight against cybercrime is far from over. As PopeyeTools’ takedown shows, law enforcement is making progress, but it’s up to us to stay informed and take charge of our online security.
I encourage you to stay up to date with the latest news on cyber threats and to adopt strong cybersecurity measures for yourself and your business. Remember, it only takes one mistake, one lapse in security, to expose your sensitive data to hackers.
Let’s be proactive, stay informed, and ensure that we are doing our part to protect ourselves from the growing threat of cybercrime.
Take a moment today to review your online security and make sure you’re not leaving your data vulnerable. The next fight against cybercrime could be your “personal” wake-up call.
By staying informed, adopting stronger cybersecurity practices, and working together to combat cybercrime, we can all help make the digital world a safer place.
Stay vigilant, stay secure!





