Table of Contents
Security researchers have exposed ShadowSyndicate (SS), a threat actor linked to multiple ransomware attacks using seven different families of ransomware.
Working together, Group-IB analysts, Bridewell, and independent researcher Michael Koczwara discovered evidence pointing to ShadowSyndicate’s involvement in ransomware campaigns dating back to July 2022.
While the actor may serve as an initial access broker (IAB), there are indications of their affiliation with various ransomware operations.
Key Takeaways:
- Multi-Ransomware Actor: The ransomware is associated with the deployment of seven ransomware families, including Quantum, Nokoyawa, BlackCat/ALPHV, Clop, Royal, Cactus, and Play.
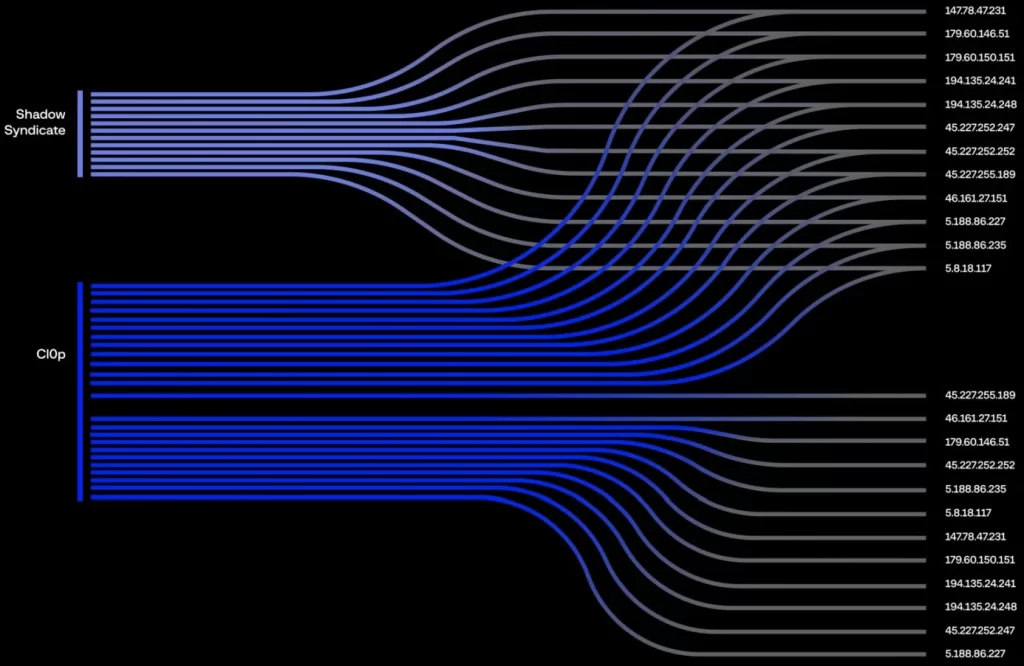
- Shared SSH Fingerprint: Researchers identified SS through a unique SSH fingerprint found on 85 IP servers, predominantly Cobalt Strike command and control machines.
- Affiliation with Ransomware Operations: While ShadowSyndicate may function as an initial access broker, evidence suggests they collaborate with multiple ransomware-as-a-service (RaaS) operations.
Unveiling ShadowSyndicate’s Arsenal
Researchers employed various tools and open-source intelligence (OSINT) techniques to uncover SS’s activities. They detected multiple Cobalt Strike watermarks (license keys) associated with ransomware attacks, indicating a wide-ranging campaign.
Diverse Server Landscape
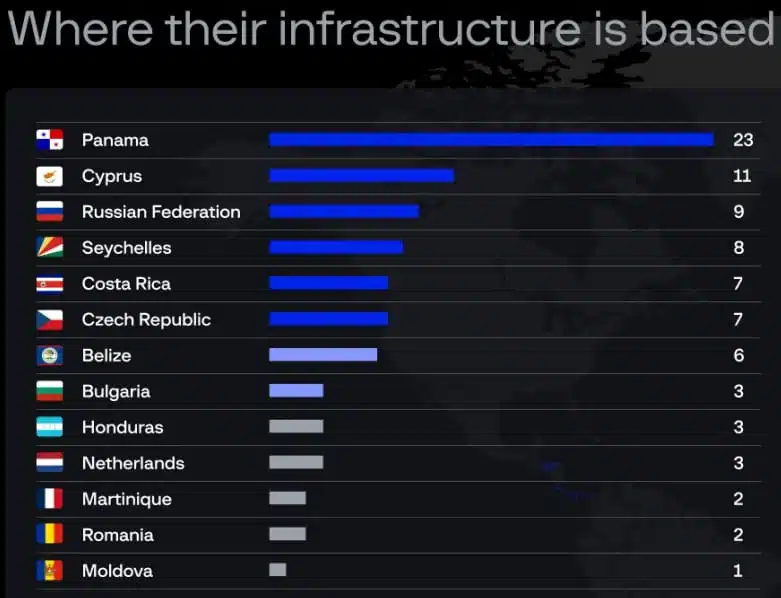
Despite the common SSH fingerprint, the analysis revealed that the 85 servers linked to ShadowSyndicate had 18 different owners, 22 network names, and 13 locations. This diversity suggests a complex infrastructure.
Linking to Ransomware Campaigns
Using Cobalt Strike command and control parameters, the analysts established strong connections between SS and ransomware attacks, including Quantum, Nokoyawa, and ALPHV/BlackCat.
Tentative Affiliation with Other Malware
While evidence suggests associations with Ryuk, Conti, Trickbot, Royal, Clop, and Play malware operations, direct links to SS remain less certain. Notably, IP addresses formerly associated with Clop ransomware have shifted to ShadowSyndicate’s control.
Affiliate in the Ransomware Ecosystem
The findings point to SS’s role as an affiliate collaborating with various ransomware-as-a-service (RaaS) operations. However, conclusive evidence is needed to support this hypothesis.

Conclusion
The identification of SS sheds light on the intricate web of ransomware operations. While affiliations are suspected, further research is required to definitively establish their role.
Collaboration among cybersecurity researchers is essential to unraveling the remaining mysteries of this threat actor’s activities.
About Group-IB: Group-IB is a cybersecurity company specializing in the prevention of cyberattacks, threat hunting, and incident response. Their research and intelligence efforts contribute significantly to understanding and countering cyber threats.