Table of Contents
WordPress Credentials Stolen via GitHub Exploit: A Widespread Cybersecurity Threat – A shocking cybersecurity revelation has emerged: over 390,000 WordPress credentials have been stolen through a malicious GitHub repository.
This alarming attack has raised concerns among website owners and developers worldwide about the safety of their data and the tools they rely on.
Key Takeaway WordPress Credentials Stolen via GitHub Exploit:
- This incident highlights the urgent need for vigilance when using third-party tools and repositories, as cybercriminals are exploiting these platforms to target users.
The Discovery of a Malicious GitHub Repository
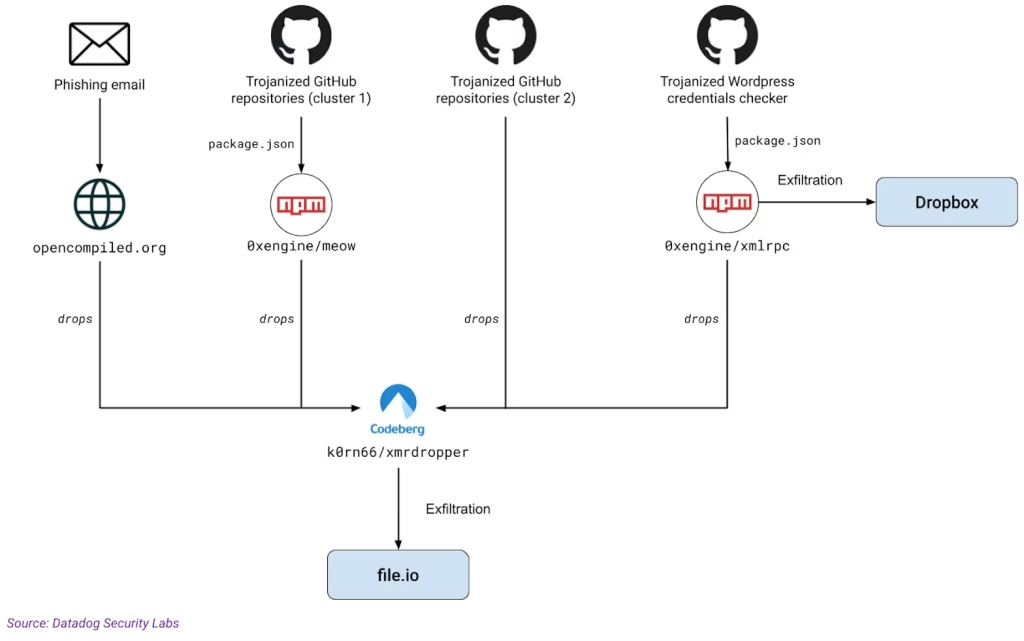
The attack came to light when researchers from Datadog Security Labs identified a threat actor, dubbed MUT-1244, exploiting GitHub repositories to steal sensitive information.
One such repository, named “yawpp,” falsely advertised itself as a WordPress tool called Yet Another WordPress Poster. However, it harbored malicious scripts designed to exfiltrate credentials.
The repository’s scripts included a rogue npm dependency that deployed malware. This malware exploited the XML-RPC API used by WordPress for remote publishing, enabling the theft of login credentials.
Before its removal, the repository facilitated the exfiltration of credentials to an attacker-controlled Dropbox account.
How the Exploit Worked
The threat actor’s approach was calculated and multifaceted:
- Fake GitHub Repositories: MUT-1244 created repositories with AI-generated profile pictures and trojanized code, luring developers seeking proof-of-concept (PoC) exploit tools.
- Phishing Emails: Emails targeted academics and developers, tricking them into running malicious commands under the guise of kernel upgrades.
- Data Exfiltration: The malware collected SSH private keys, AWS credentials, and other sensitive data, sending it to external servers for exploitation.
- Second-Stage Payloads: These included backdoored files, malicious PDFs, Python droppers, and npm packages like 0xengine/meow.
Impact on Victims
The victims included security researchers, penetration testers, and even malicious actors who inadvertently exposed their data. Datadog’s analysis revealed that this attack not only compromised credentials but also allowed the threat actor to:
- Access private SSH keys.
- Steal AWS environment variables.
- Retrieve command histories.
- Gain insights into sensitive corporate infrastructure.
In total, the stolen WordPress credentials impacted thousands of websites, potentially putting their users and data at risk.
Why Are WordPress Credentials a Prime Target?
WordPress powers over 43% of websites globally, making it a lucrative target for cybercriminals. By stealing credentials, attackers can:
- Gain unauthorized access to websites.
- Install malware or deface pages.
- Steal customer data or launch further attacks.
Real-Life Example: Similar tactics were observed in 2022 when attackers used malicious npm packages to steal sensitive data.
Preventive Measures for Developers and Site Owners
This incident underscores the need for proactive security measures:
| Action | Description |
|---|---|
| Verify Repositories | Only use repositories from verified and reputable sources. |
| Audit Dependencies | Regularly check npm or other package dependencies for malicious code. |
| Use MFA | Implement Multi-Factor Authentication for all logins. |
| Regular Backups | Keep backups of your site to restore data in case of a breach. |
| Educate Team Members | Train your team to recognize phishing attempts and avoid risky commands. |
How GitHub and npm Responded
GitHub promptly removed the malicious repository upon discovery. Similarly, the npm package, which had been active for over a year with 1,790 downloads, was taken down.
These swift actions demonstrate the importance of monitoring and responding to security threats in developer ecosystems.
However, this incident is a reminder that users must exercise caution and not solely rely on platform interventions to stay secure.
About Datadog Security Labs
Datadog Security Labs is a leading provider of cloud monitoring and security solutions. Their team specializes in identifying vulnerabilities and protecting digital ecosystems. For more information, visit their official website.
Rounding Up
The theft of WordPress credentials via a GitHub exploit highlights the growing sophistication of cyberattacks targeting developers and website owners. By staying informed and adopting robust security practices, you can reduce your risk and safeguard your data.
Remember, prevention is always better than cure in the digital age.
FAQs
How can I check if my WordPress credentials were stolen?
- Monitor your account for unauthorized access and change your password immediately. Enable MFA for added security.
What is XML-RPC in WordPress?
- XML-RPC is a protocol that allows remote access to WordPress sites, often used for publishing content or managing sites remotely.
How do I verify the safety of a GitHub repository?
- Look for verified badges, check the contributor’s activity, and read user reviews before downloading any code.
What are the risks of using malicious npm packages?
- Malicious npm packages can steal data, inject malware, or compromise the systems they are installed on.
How can developers stay safe from such attacks?
- Regularly audit your tools, avoid unverified sources, and stay updated on cybersecurity best practices.





