Table of Contents
Cybersecurity researchers have revealed that the Russian cyber group Secret Blizzard is behind recent sophisticated cyberattacks targeting Ukrainian military and government entities.
The group, known for its stealth and resourcefulness, has been leveraging tools and infrastructure stolen from other hacking groups to carry out its campaigns.
This strategy includes deploying custom malware such as the Tavdig and KazuarV2 backdoors, highlighting a calculated approach to intelligence gathering. These activities underline the growing threat posed by nation-state actors in the digital warfare landscape.
Key Takeaway to Russian Cyber Group Secret Blizzard:
Secret Blizzard’s cyberattacks underscore the persistent and evolving threat of cyber espionage in geopolitical conflicts.
A Deeper Look Into Secret Blizzard’s Campaign
Leveraging Stolen Tools and Techniques
From March to April 2024, the Russian cyber group Secret Blizzard used tools like the Amadey bot malware, commonly linked to cybercriminal operations, to breach Ukrainian targets.
This marks at least the second time since 2022 that the group has utilized such tactics to deploy its backdoors, Tavdig and KazuarV2.
The group gained access to systems by exploiting compromised tools from other threat actors like Storm-1919 and Storm-1837. These tools were used to infiltrate devices linked to Ukrainian military operations, especially those utilizing Starlink connections.
How the Attacks Were Executed
The attack typically began with a PowerShell dropper loaded with malware such as Amadey bots. This malware gathered sensitive system information, including antivirus status and user credentials.
| Malware Used | Functionality |
|---|---|
| Amadey Bot | Collects system data and deploys cryptocurrency miners or malware |
| Tavdig Backdoor | Enables reconnaissance and establishes persistence |
| KazuarV2 Backdoor | Facilitates command-and-control operations |
The collected information was sent back to Secret Blizzard’s servers, enabling further attacks or data theft.
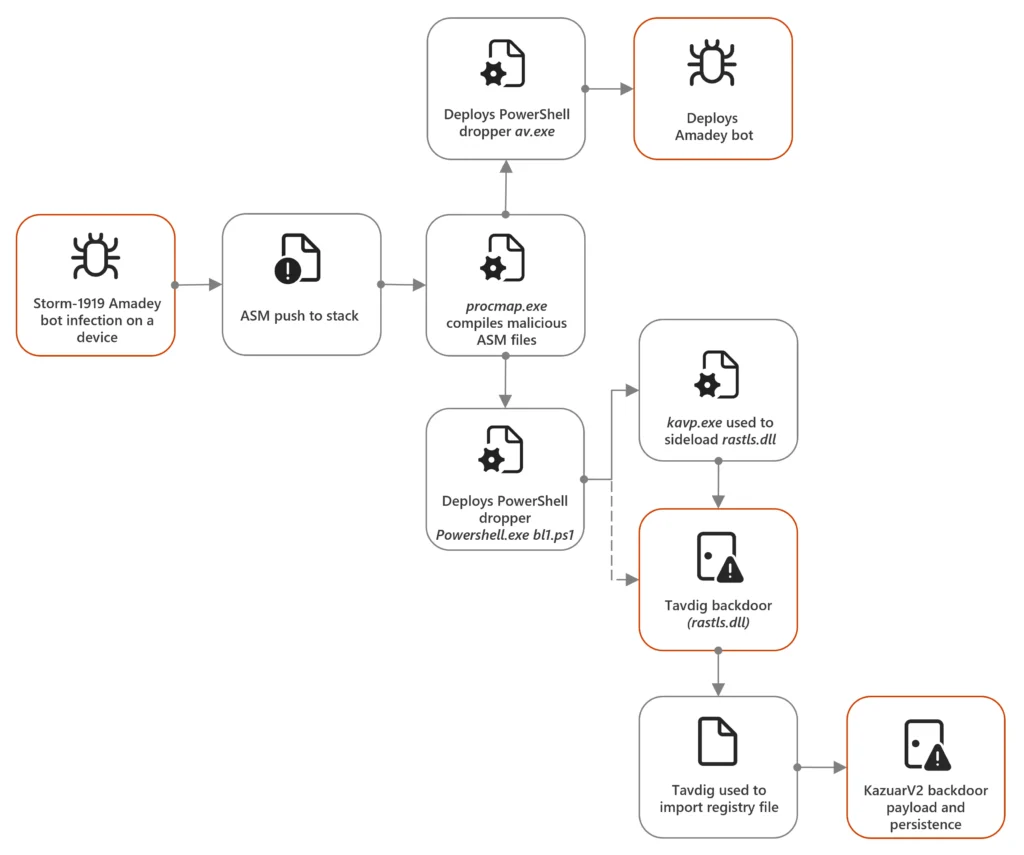
The Group’s Unique Strategy
Commandeering Cybercrime Campaigns
One striking feature of the Russian cyber group Secret Blizzard is its ability to hijack the operations of other threat actors. For example, it repurposed the tools of Storm-1837, a group targeting Ukrainian drone operators, to deploy its own malware.
These efforts were bolstered by strategic web compromises and spear-phishing campaigns that allowed Secret Blizzard to infiltrate and navigate secure networks.
Not Just Military Targets
While the group’s primary focus is on military and government institutions, its reach extends to foreign ministries, embassies, and even private companies. Their use of advanced tools and strategies indicates a well-resourced and state-backed operation.
A Real-Life Example of Cyber Espionage
This approach mirrors a previous attack in 2020, where Russian-linked hackers infiltrated SolarWinds, compromising U.S. government agencies and corporations worldwide. You can read more about the SolarWinds breach here.
What Organizations Can Learn
Cybersecurity professionals emphasize the importance of proactive defense. Organizations can protect themselves by:
- Regularly updating software and security patches.
- Monitoring for unusual network activity.
- Training employees to recognize phishing attempts.
Microsoft and other companies continue to notify compromised organizations and offer guidance to secure their systems.
About Secret Blizzard
Secret Blizzard, also known as Turla or Venomous Bear, is attributed to Russia’s Federal Security Service (FSB). The group specializes in cyber espionage, focusing on political and military intelligence.
Rounding Up
The Russian cyber group Secret Blizzard represents a significant threat in the evolving landscape of cyber warfare. Their ability to leverage stolen tools and adapt to new strategies underscores the importance of robust cybersecurity measures. As organizations face an increasing risk of multi-vector attacks, staying vigilant is critical.
FAQs
Who is Secret Blizzard?
Secret Blizzard is a Russian nation-state cyber group associated with the FSB. It is known for its advanced cyber espionage activities worldwide.
What are Tavdig and KazuarV2?
Tavdig and KazuarV2 are backdoor malware used by Secret Blizzard for reconnaissance, data theft, and maintaining persistence in targeted systems.
How can organizations protect against similar attacks?
Organizations can safeguard against such threats by regularly updating systems, using multi-factor authentication, and monitoring for unusual activity.
Are such attacks common?
Yes, nation-state cyberattacks have been increasing, especially in regions with geopolitical tensions.





