Table of Contents
A new malware tool, recognized as EDRKillShifter, has emerged from the RansomHub gang, enhancing their ransomware capabilities by evading endpoint detection and response (EDR) systems, escalating concerns in the cybersecurity community.
Short Summary of the New Malware:
- The RansomHub gang has introduced EDRKillShifter, a tool designed to bypass robust endpoint protection.
- The malware has already attacked organizations, showcasing its potency in ransomware operations.
- Experts emphasize the importance of robust cybersecurity measures to counteract evolving threats like EDRKillShifter.
In recent developments, the infamous RansomHub gang has captured cybersecurity experts’ attention by unveiling a malicious tool, EDRKillShifter.
This new addition is designed specifically to overcome the latest EDR systems that organizations rely on to safeguard their endpoints. The gang, rapidly growing in notoriety since its inception earlier this year, has already utilized this tool in several attacks, raising alarms about the increasing sophistication of cybercriminal enterprises.
According to reports, RansomHub operates as a ransomware-as-a-service (RaaS) group, leasing its malicious software to various affiliates who perform the actual attacks.
Their strategy involves the distribution of ransomware and focusing on evading detection mechanisms, contributing to the alarming rise in successful ransomware incidents.
Security analysts state that EDRKillShifter represents a significant leap in the operational tactics of ransomware groups.
The Emergence of EDRKillShifter
EDRKillShifter is said to function as a ‘loader’ executable, facilitating the deployment of payloads that target and disable existing security solutions on infected computers.
Its primary function is to execute a legitimate driver that is known to have vulnerabilities, enabling the attackers to manipulate system permissions to disable endpoint protection.
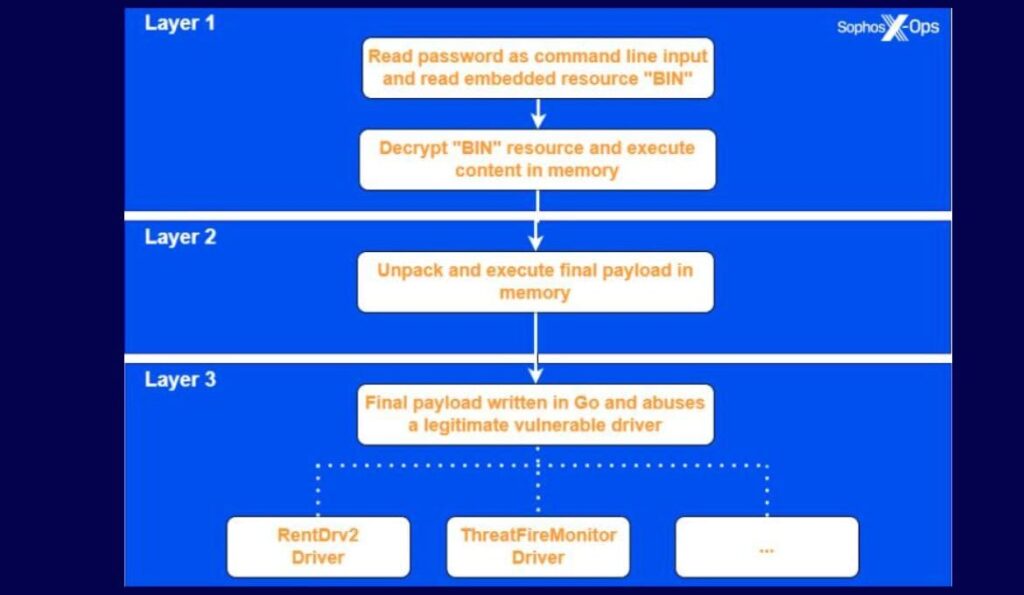
The operation of EDRKillShifter occurs in a three-step process. Initial execution requires a password string, which, when correctly entered, unlocks the payload contained within.
This payload is structured to exploit a legitimate driver, allowing the attackers to unhook, or disable, defenses provided by EDR systems.
“This descriptive mechanism highlights the strengths of EDRKillShifter, showcasing its innovative approach to bypassing modern detection tools,” stated a cybersecurity analyst at SentinelLabs.
The Evolution of RansomHub
RansomHub’s growth in the cybercrime landscape is believed to parallel the fall of other ransomware groups such as LockBit, whose disruption by global law enforcement agencies led many affiliates to seek refuge in RansomHub’s services.
Notably, RansomHub has been actively recruiting former members from the now-defunct ALPHV group, amplifying its ranks and capabilities.
In its brief existence, RansomHub has managed to climb the ranks of ransomware groups by cleverly leveraging the talents of disgruntled affiliates from other failed operations.
This recruitment strategy aligns with a growing trend in the cybercrime landscape where groups capitalize on former members’ expertise to bolster their operations.
Operational Tactics and Implications
Reports indicate that RansomHub utilizes a method of exfiltrating sensitive data before launching ransomware attacks, a tactic seen in multiple high-profile incidents. The gang primarily operates through cybercriminal forums, where they facilitate their RaaS business model and share updates about their latest exploits.
This systematic approach of initial data theft followed by encryption and ransom appeals—combined with tools like EDRKillShifter—reinforces the substantial threat this group poses to enterprises worldwide.
“The emergence of EDRKillShifter in their toolkit illustrates a troubling trend where cybercriminals are increasingly skillful in manipulating technology to evade security measures,” expressed Fenix24’s co-founder, Heath Renfrow.
Recent Attacks and Demonstrations of Power
RansomHub’s recent campaign highlights the group’s growing assertiveness—an incident involving the Florida Department of Health exemplifies this, where the gang leaked terabytes of sensitive information after negotiation breakdowns over ransom demands.
Similarly, RansomHub claimed responsibility for various attacks against corporations across sectors, including healthcare and finance, underscoring its ability to strike critical infrastructure.
By evading established security protocols with tools like EDRKillShifter, RansomHub increases the difficulty for organizations trying to secure their networks. Experts highlight that as ransomware threats become more advanced, businesses must evaluate and reinforce their cybersecurity frameworks.
Preventative Measures and Recommendations
To navigate this evolving threat landscape, cybersecurity experts recommend several proactive measures:
- Implementing robust EDR solutions that ensure tamper protection and behavioral analysis.
- Maintaining regular backups and ensuring they are offline to prevent ransomware access.
- Conducting regular security audits to catch vulnerabilities before they can be exploited.
- Enforcing the principle of least privilege, and ensuring that users have only the access necessary for their roles.
- Educating employees on the risks and preventative measures associated with ransomware attacks.
Organizations must adopt a multi-faceted defense strategy encompassing prevention, detection, and response measures to counteract the threats presented by RansomHub and similar groups,” noted a cybersecurity consultant.
The Road Ahead
As we move forward in 2024, the activities of RansomHub and its deployment of EDRKillShifter signal a critical juncture in the ransomware battle. This emerging gang, characterized by its quick adaptability and innovative malware toolsets, marks a concerning trend within the cybercrime landscape where EDR circumventing tools are increasingly prevalent.
The adaptability shown by RansomHub raises red flags for enterprises that depend on EDR systems alone to protect their sensitive data. By continuing to monitor and assess the development of such threats, businesses can strategically prepare to defend against the looming specter of ransomware.
In conclusion, RansomHub’s swift rise and the introduction of EDRKillShifter are reminders of the relentless evolution of cyber threats. Protecting against these threats requires vigilance, innovation, and a willingness to enhance existing security postures to mitigate risks in this challenging environment.
Organizations must not only invest in advanced security tools but also foster a company culture of cybersecurity awareness—not only to safeguard their assets but to navigate the complexities of a world increasingly threatened by sophisticated ransomware operations.





