Table of Contents
P2PInfect Botnet Surges with 600X Traffic Increase: Security experts are raising alarm bells over a substantial surge in P2PInfect botnet activity since late August 2023, with an astounding 600-fold spike observed between September 12 and 19, 2023.
This concerning escalation has drawn attention due to the botnet’s ability to target Redis servers across Linux and Windows systems.
Key Takeaways to P2PInfect Botnet Surges with 600X Traffic Increase:
- P2PInfect botnet activity has witnessed an astonishing 600-fold increase since late August 2023.
- This botnet leverages a P2P worm that targets Redis servers on both Linux and Windows operating systems, making it exceptionally potent and scalable.
- The surge in botnet traffic correlates with an increase in variants detected in the wild, implying active development and enhancement by its creators.
The Potent P2PInfect Worm
In July 2023, researchers at Palo Alto Networks Unit 42 uncovered a potent peer-to-peer (P2P) worm named P2PInfect. This worm stands out for its capacity to target Redis servers running on both Linux and Windows systems.
The worm is crafted using the Rust programming language and exploits the Lua sandbox escape vulnerability CVE-2022-0543 with a CVSS score of 10.0.
A Staggering Traffic Surge
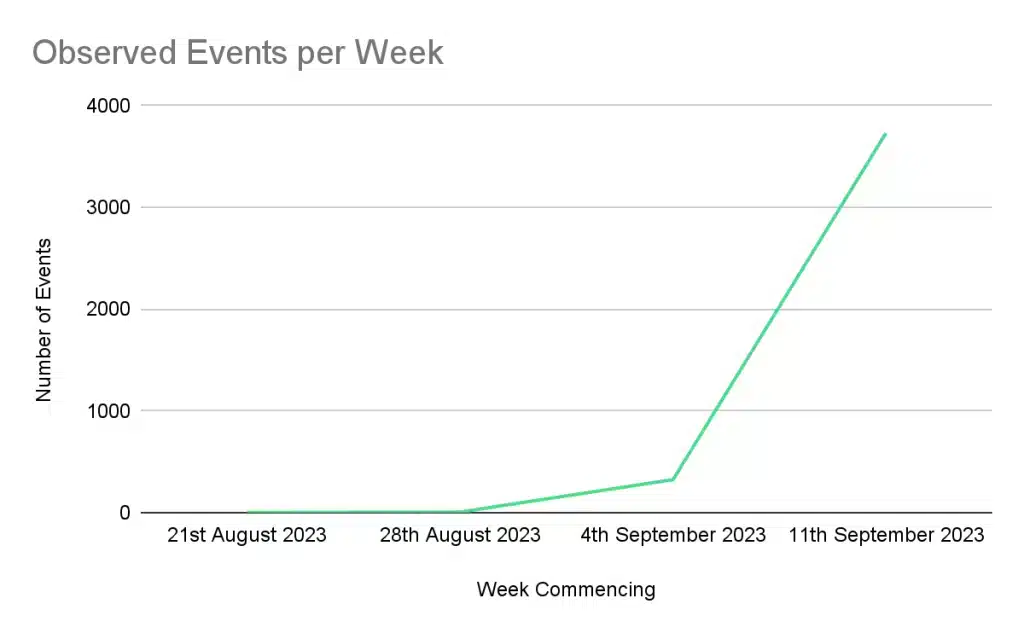
Cado Security Labs has reported a staggering 600-fold increase in P2PInfect traffic since August 28th, with a notable 12.3% surge in the week leading up to their analysis publication.
The botnet’s reach has extended to multiple countries, including China, the United States, Germany, the United Kingdom, Singapore, Hong Kong, and Japan.
Active Botnet Development and Variants
The surge in botnet activity is attributed to the proliferation of variants detected in the wild. This dynamic suggests that the botnet’s creators are actively refining and improving their malicious creations.
The number of observed P2Pinfect events spiked to 3,619 during the week of September 12th to 19th, signifying a staggering 60,216.7% increase.
Attack Chain Insights
Researchers have outlined the attack chain employed by P2PInfect. It involves an initial malicious node establishing a connection with the target, exploiting Redis vulnerabilities to execute arbitrary shell commands, and deploying a designated downloader node to fetch and execute payloads.
Subsequently, the attacker removes the Redis module, ensuring minimal traceability.
Persistence Mechanisms and Password Changes
While the original P2PInfect bot lacked persistence, recent samples have adopted a cron job to launch the malware every 30 minutes.
Additionally, newer variants support another persistence technique using a bash payload to maintain the main payload’s operation. These samples also overwrite existing SSH authorized_keys files with attacker-controlled SSH keys.
The primary payload of P2PInfect iterates through system users, attempting to change their passwords to a pattern prefixed by “Pa_” and followed by seven alphanumeric characters.
This behavior, likely to obtain root access, generates new passwords with each build.
Unclear Objectives and Cryptomining
Despite its growing sophistication, the exact objectives of P2PInfect remain unclear. While the malware attempts to fetch a crypto miner payload, there is no evidence of crypto mining to date.
The report concludes that the botnet’s operators are actively developing its capabilities, suggesting potential future activities or intentions to sell access to other threat actors.
Conclusion
The alarming surge in P2PInfect botnet activity underscores the evolving landscape of cyber threats. With its capacity to target Redis servers across multiple platforms, this botnet poses a significant risk. Its creators’ commitment to ongoing development and refinement raises concerns about future cyber threats and their potential impact.
About Palo Alto Networks Unit 42 and Cado Security Labs:
Palo Alto Networks Unit 42 is a renowned cybersecurity research team that specializes in threat intelligence and analysis. Cado Security Labs is a cybersecurity research organization dedicated to analyzing and mitigating emerging cyber threats. Both entities play critical roles in uncovering and understanding advanced cyber threats.