Table of Contents
New P2PInfect Worm: A Menace to Redis Servers on Linux and Windows: A new cloud-targeting, peer-to-peer worm called P2PInfect has been identified by cybersecurity researchers. This worm exploits vulnerable Redis instances on both Linux and Windows systems, making it more powerful and scalable than other worms.
Written in Rust, a cloud-friendly programming language, P2PInfect leverages a critical Lua sandbox escape vulnerability to infect systems and establish a peer-to-peer network for malicious activities.
Key Takeaways on New P2PInfect Worm:
- P2PInfect: A new cloud-targeting worm infecting Redis instances on Linux and Windows systems.
- Critical Vulnerability: The worm exploits CVE-2022-0543, a Lua sandbox escape vulnerability, to gain initial access and propagate malware.
- Peer-to-Peer Communication: P2PInfect establishes a peer-to-peer network to distribute malicious payloads and maintain persistent access.
Security researchers have discovered a new and potent worm named P2PInfect that poses a significant threat to Redis servers running on Linux and Windows operating systems.
Unlike traditional worms, P2PInfect utilizes a cloud-targeting strategy combined with peer-to-peer (P2P) communication, making it a more scalable and dangerous cyber threat.
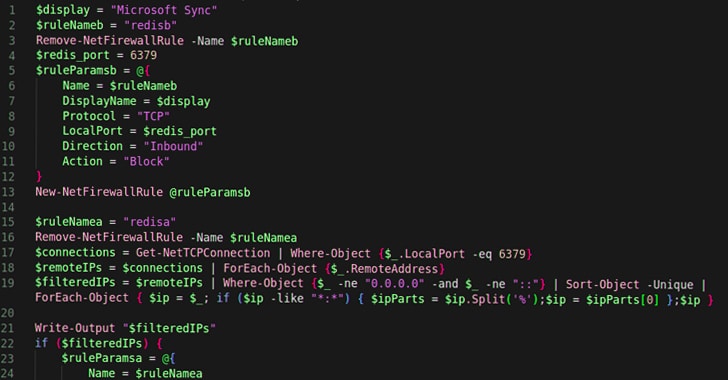
Crafted using Rust, a highly adaptable programming language, this worm exploits a critical vulnerability to infiltrate vulnerable Redis instances and execute follow-on exploitation.
Exploiting Redis Vulnerabilities: The Path of P2PInfect
P2PInfect takes advantage of a critical Lua sandbox escape vulnerability known as CVE-2022-0543 (CVSS score: 10.0), which has been previously leveraged to deliver various malware families.
The worm’s initial access is established through this exploit, allowing it to deploy a dropper payload. This payload creates a peer-to-peer (P2P) communication channel, connecting to a larger network to fetch additional malicious binaries.
The malware’s scanning software is then used to propagate the infection to other exposed Redis and SSH hosts, amplifying the worm’s impact.
Persistent Access and Self-Update Mechanism
Once infected, the compromised Redis instance becomes part of the P2P network, offering future compromised systems access to the malicious payloads.
To ensure persistent access, the malware employs a PowerShell script to establish and maintain communication between the compromised host and the P2P network.
The Windows variant of P2PInfect incorporates a Monitor component that allows it to self-update and launch new versions, making it harder to detect and eradicate.
Elusive End Goal and Attribution
The ultimate objective of the P2PInfect campaign remains uncertain. Although the toolkit’s source code contains the term “miner,” there is no definitive evidence of cryptojacking yet.
The activity has not been attributed to any known threat actor groups typically associated with cloud-targeting or cryptojacking attacks. The worm’s design and the establishment of a P2P network for malware auto-propagation are unusual in the cloud threat landscape, reflecting its sophistication and unique characteristics.
The Prevalence of Misconfigured and Vulnerable Cloud Assets
As cybercriminals constantly scan the internet for misconfigured and vulnerable cloud assets, sophisticated attacks are being launched within minutes of discovery.
P2PInfect’s design choices and modern development techniques distinguish it from traditional cloud-targeting threats, raising concerns among cybersecurity researchers.
Conclusion
The emergence of P2PInfect poses a serious threat to Redis servers on Linux and Windows systems, demonstrating the evolving sophistication of cyber threats in cloud environments. By exploiting critical vulnerabilities and establishing peer-to-peer communication, this worm exhibits a unique and potent attack strategy.
The cybersecurity community remains vigilant in tracking and mitigating such advanced threats, emphasizing the importance of robust security measures and regular system audits to safeguard against emerging cyber risks.





