Table of Contents
Microsoft Detects Attackers Targeting Azure Cloud VMs via Breached SQL Servers: Microsoft’s cybersecurity experts have identified a concerning cyberattack campaign in which hackers attempted to gain access to a cloud environment by exploiting an SQL Server instance.
This technique, although common in cloud services like VMs and Kubernetes clusters, is novel when applied to SQL Server.
The attackers initiated their assault by exploiting a SQL injection vulnerability within the target’s environment, eventually trying to move laterally to other cloud resources by manipulating the server’s cloud identity.
This incident underscores the critical importance of securing cloud identities to prevent unauthorized access to SQL Server instances and cloud resources.
Key Takeaways to Microsoft Detects Attackers Targeting Azure Cloud VMs via Breached SQL Servers:
- Attack on Azure Cloud VMs via SQL Servers: Microsoft has detected a cyberattack where hackers attempted to infiltrate Azure Virtual Machine (VM) environments by first exploiting an SQL injection vulnerability. This breach allowed them to gain elevated permissions on a Microsoft SQL Server instance.
- Abuse of Cloud Identities: The attackers subsequently attempted to move laterally within the cloud environment by exploiting the cloud identity of the compromised server. Cloud identities, often used in cloud services like SQL Server, can possess elevated permissions for cloud actions.
- Cloud-Based Attack Techniques: As organizations increasingly migrate to the cloud, attackers are developing new methods for lateral movement within cloud environments. This includes abusing cloud identities, which introduces potential security risks.
Attack on Azure Cloud VMs via SQL Servers
Microsoft has detected a sophisticated cyberattack that targeted Azure cloud environments.
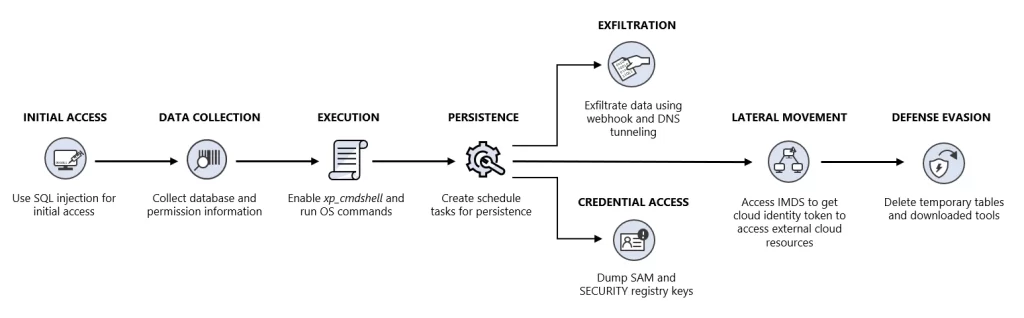
In a departure from typical attack vectors, the hackers initiated their assault by exploiting a SQL injection vulnerability present within the target’s environment.
This initial breach allowed them to gain access and elevate their permissions on a Microsoft SQL Server instance hosted in Azure Virtual Machines (VMs).
Abuse of Cloud Identities
Subsequently, the attackers sought to move laterally within the cloud environment by leveraging the cloud identity associated with the compromised server. Cloud services, including Azure, utilize managed identities to authenticate and authorize interactions between various cloud resources and services.
While managed identities offer convenience and efficiency, they also introduce potential security vulnerabilities.
For instance, if attackers compromise a VM, they can obtain an access token for its associated identity by querying the instance metadata service (IMDS) endpoint. Armed with this access token, attackers can perform various malicious actions on cloud resources accessible to that identity.
In this specific attack, the hackers attempted to perform identity-based lateral movement, a technique not previously observed in SQL Server instances.
Cloud-Based Attack Techniques
The evolving landscape of cloud computing has introduced new attack techniques distinct from those encountered in traditional on-premises environments. Attackers are now exploring novel methods to move laterally from on-premises environments into cloud resources.
One such method involves abusing cloud identities associated with cloud resources. In this context, the attackers targeted SQL Server instances, attempting to exploit the cloud identity associated with these servers.
While this approach may be new, the attack shared common characteristics with typical SQL Server attacks, including the initial exploitation of a SQL injection vulnerability.
The attackers used this initial access to collect critical information about the host, databases, and network configuration. They also enabled the xp_cmdshell command, allowing them to execute operating system commands via SQL queries.
This facilitated data collection, persistence, and attempts to obtain credentials.
For data exfiltration, the attackers employed a unique method involving a publicly accessible service called “webhook.site,” enabling discreet transmission of outgoing traffic.
Recommendations for Defenders
While this attack did not succeed in moving laterally within the cloud environment, it highlights the importance of safeguarding cloud identities. Defenders should consider the following best practices to protect their environments against similar attacks:
- Monitor for SQL injection vulnerabilities and apply appropriate patches and security measures.
- Restrict permissions and access to sensitive cloud resources, particularly for managed identities.
- Continuously monitor for suspicious activity, especially unauthorized access attempts.
- Implement robust security practices to prevent and mitigate lateral movement within cloud environments.
Conclusion
The evolving cloud landscape presents new challenges for cybersecurity. Attackers are continually devising innovative techniques to exploit vulnerabilities and move laterally within cloud environments.
Vigilance, proactive security measures, and a deep understanding of cloud-specific risks are essential to protect organizations from these evolving threats.
About Microsoft:
- Microsoft: Microsoft is a multinational technology company known for its software, cloud services, and hardware products. It is a leader in the technology industry, providing a wide range of solutions for individuals and businesses globally, including the Azure cloud computing platform.





