Table of Contents
Lazarus Group Launders $900 Million in Cryptocurrency: Cryptocurrency laundering, to the tune of billions, has been linked to the notorious North Korean Lazarus Group.
Between July 2022 and July of this year, the group is suspected to have illicitly obtained around $900 million through these illicit activities.
Key Takeaways to Lazarus Group Launders $900 Million in Cryptocurrency:
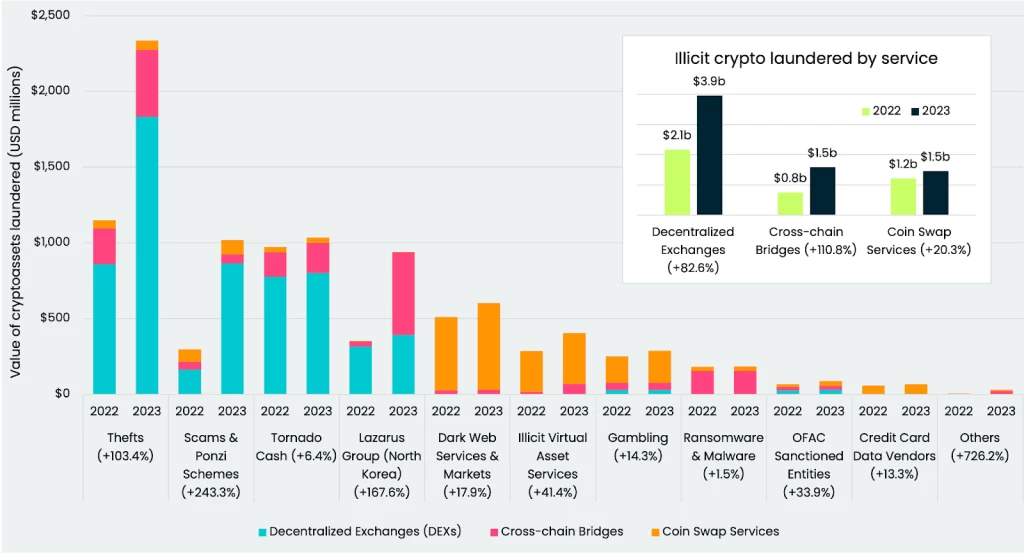
- Rising Cross-Chain Crime: Cryptocurrency laundering is shifting towards cross-chain methods, with blockchain analytics firm Elliptic reporting a surge in such activities. Traditional entities like mixers are increasingly targeted and scrutinized.
- Lazarus Group’s Heist: The Lazarus Group, believed to be of North Korean origin, has been responsible for stealing nearly $240 million in cryptocurrency since June 2023. Their targets include Atomic Wallet, CoinsPaid, Alphapo, Stake.com, and CoinEx.
- Money Laundering Typology: The Lazarus Group employs cross-chain bridges and ‘chain-hopping’ techniques to obfuscate the origin of stolen cryptocurrency. This method is recognized as a money laundering typology.
Rising Cross-Chain Crime
Cryptocurrency laundering is undergoing a significant transformation, with criminals turning to cross-chain methods. These techniques involve rapidly converting cryptocurrency assets from one token or blockchain to another, making it challenging to trace the funds’ origin.
As a result, money launderers are increasingly using cross-chain approaches to evade detection, especially since traditional methods like mixers are facing heightened seizures and sanctions.
Lazarus Group’s Heist
The Lazarus Group, a threat actor with alleged North Korean ties, has emerged as a major player in cryptocurrency theft. Since June 2023, they have managed to steal nearly $240 million in cryptocurrency through a series of high-profile attacks. Some of their notable targets include:
- Atomic Wallet ($100 million)
- CoinsPaid ($37.3 million)
- Alphapo ($60 million)
- Stake.com ($41 million)
- CoinEx ($31 million)
This group is known for its diversity in tactics, including cyber espionage, cyber sabotage, and financial gain.
Money Laundering Typology: Chain-Hopping
Elliptic, a blockchain analytics firm, has observed the Lazarus Group’s use of cross-chain bridges to launder their ill-gotten gains.
This approach has contributed to a staggering 111% increase in the proportion of funds sent via such services. The act of moving cryptocurrency assets back and forth between chains, known as ‘chain-hopping,’ is now recognized as a money laundering typology.
These transactions have no legitimate business purpose other than to obscure the origin of the stolen funds.
South Korea’s Alert
The revelation about the Lazarus Group’s cryptocurrency laundering activities comes in the wake of South Korea’s National Intelligence Service (NIS) warning about North Korea’s cyberattacks on its shipbuilding sector.
The North Korean hackers primarily target IT maintenance companies, utilizing methods such as occupying and bypassing PCs and distributing phishing emails to internal employees.
Conclusion
Cryptocurrency laundering continues to evolve, with criminal groups like the Lazarus Group adapting to new methods. Cross-chain crime and ‘chain-hopping’ have become prominent in the world of illicit cryptocurrency activities. Authorities and cybersecurity experts face ongoing challenges in combatting these threats.
About the Lazarus Group:
The Lazarus Group is a notorious threat actor believed to have North Korean ties. They are known for a wide range of cyber activities, including espionage, sabotage, and financial crimes. This group has targeted various cryptocurrency platforms and organizations, accumulating substantial funds through illicit means.





