Table of Contents
Google Exposes GLASSBRIDGE: The emergence of Storm-2077 marks a new chapter in cyber threats, particularly from state-sponsored actors in China.
Active since at least January 2024, this group has targeted various sectors, including government agencies and the Defense Industrial Base, showcasing a sophisticated approach to cyber warfare that goes beyond mere hacking into complex information-gathering missions.
Targeted Sectors and Recent Activities
Little is known about the full extent of Storm-2077’s operations, but it has proven successful in leveraging phishing attacks and exploiting vulnerabilities in internet-facing devices.
Notably, this group has conducted cyber-attacks across diverse sectors like aviation, telecommunications, and financial services, indicating a broad ambition to infiltrate both public and private entities worldwide.
This group’s activities highlight a systematic effort to harvest sensitive credentials, gaining access to cloud environments and eDiscovery applications. As discovered by Microsoft, Storm-2077 has utilized open-source malware like Cobalt Strike and Pantegana to further its operations.
This attack methodology not only compromises sensitive data but also enables further espionage, thereby jeopardizing your organization’s security standing and integrity in a global context.
Attack Methods and Techniques
Insights into the techniques employed by Storm-2077 reveal a sophisticated approach in cyber operations. Leveraging publicly available exploits, they gain initial access to internet-facing edge devices, dropping malware such as Cobalt Strike and open-source tools like Pantegana and Spark RAT.
This multifaceted strategy allows them to infiltrate various sectors, including the Defense Industrial Base and financial services, enhancing their capacity for surveillance and disruption.
Intelligence-Gathering Operations
Little is known about the intelligence-gathering missions orchestrated by Storm-2077, yet their use of phishing emails effectively compromises credentials related to eDiscovery applications.
This tactic facilitates the exfiltration of emails containing sensitive information that can significantly aid their cyber operations.
Findings suggest that Storm-2077’s operations extend beyond mere data theft. By gaining access to cloud environments through harvested credentials, they can create applications with mail read rights, allowing them to monitor communications and gather intelligence undetected.
This method not only amplifies their data collection capabilities but also poses increased risks to organizations worldwide, as sensitive information can be exploited to further their agendas.
Description of the Pro-China Influence Network
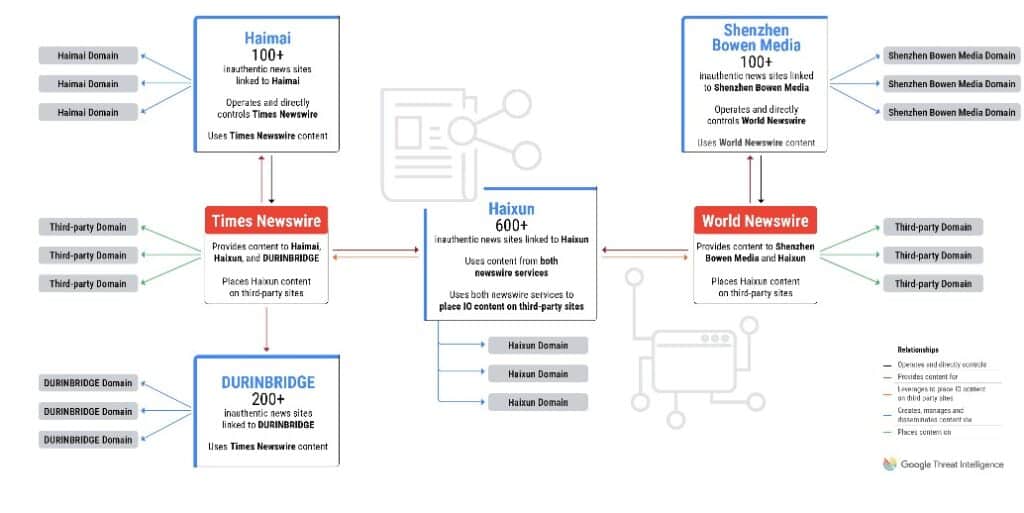
While evaluating the landscape of digital information, you will find that GLASSBRIDGE operates a network of inauthentic news sites designed to promote pro-China narratives. Managed by a few digital PR firms, these outlets masquerade as independent sources, republishing content from official Chinese state media and other commissioned materials.
Google has blocked over a thousand of these sites since 2022, highlighting their extensive reach and influence across various platforms.
Tactics Used to Manipulate News and Information
While examining GLASSBRIDGE’s methods, it becomes evident that the network uses sophisticated tactics to manipulate news and information.
By utilizing techniques beyond traditional social media, these actors create seemingly legitimate local news outlets that tailor their content to specific audiences, thereby amplifying their political agendas.
With the evolution of information operations, you should recognize that GLASSBRIDGE employs deceptive strategies to disseminate its messaging.
This includes leveraging subdomains of credible news outlets like post-gazette.com and buffalonews.com, making their content appear trustworthy and legitimate.
By presenting articles that align with Chinese interests as local news, this network successfully embeds its narratives within mainstream discourse, ultimately influencing public perception on a global scale.
Challenges of Attribution and Tracking
Now, tracking and attributing cyber threats, especially from state actors like Storm-2077, presents significant challenges for cybersecurity experts.
As attackers evolve their tactics, exploiting a wide array of vulnerabilities and employing advanced methods such as credential harvesting, it becomes increasingly difficult for you to pinpoint sources or predict future activities.
This complexity is compounded when these actors operate under multiple guises, making their operations seem legitimate, which can obscure their true intent and origin.
Responses from Tech Companies and Governments
Security measures are being ramped up as tech companies and governments recognize the need to counteract state-sponsored influence operations like GLASSBRIDGE effectively.
Google has blocked over a thousand inauthentic sites linked to this pro-China network from its news platforms, highlighting a proactive approach to safeguard information integrity.
Similarly, companies like Microsoft have also reported on tracking these activities, urging other organizations to bolster their own defenses against such sophisticated cyber threats.
Attribution of these cyber campaigns is vital for your understanding of the evolving threat landscape. You should be aware that tech companies are collaborating closely with government agencies to enhance detection and attribution capabilities.
This partnership aims to share intelligence on threats, refine tracking methodologies, and develop better defenses against malicious actors.
By staying informed about these responses, you can better anticipate the tactics employed by adversaries and protect against potential breaches of sensitive information.
To wrap up
Taking this into account, you should be aware of the complexities surrounding the pro-China influence network known as GLASSBRIDGE, which utilizes inauthentic news sites to manipulate narratives on a global scale. With over a thousand sites blocked by Google since 2022, it is clear that these operations aim to masquerade as legitimate media outlets.
As this landscape evolves, your vigilance in identifying misinformation and understanding the underlying tactics can help you navigate the information ecosystem more effectively.





