Table of Contents
Fake Captchas are spreading malware through a deceptive tactic called “DeceptionAds,” exposing unsuspecting users to serious cybersecurity risks.
These fraudulent ads, disguised as legitimate CAPTCHA verification requests, lure victims into downloading infostealer malware, which then harvests sensitive data like passwords, financial details, and personal information.
This alarming trend highlights the dark side of internet advertising, where attackers exploit user trust and online habits to execute their malicious campaigns.
Understanding how these Fake Captchas spread malware is crucial for protecting your digital footprint.

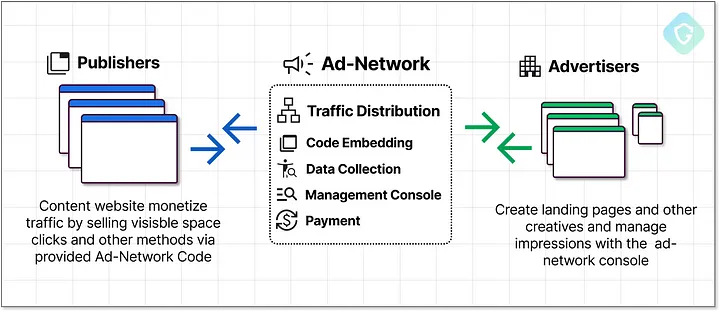
Understanding Malvertising
To grasp the impact of malvertising, you need to recognize how deceptive advertisements can be used to direct you to harmful sites.
These malicious ads disguise themselves as legitimate content, often relying on familiar elements like fake captchas to trick users into executing harmful scripts.
As demonstrated by the recent fake captcha campaign, which generated over 1 million ad impressions daily, malvertising leverages a network of seemingly innocent sites to propagate malware at an alarming scale, targeting your personal information and financial security.
Historical Context and Current Trends
Malvertising has evolved significantly over the years, growing from simple pop-up ads into sophisticated tactics that exploit the ad tech ecosystem.
This shift reflects the increasing sophistication of cybercriminals who leverage ad networks like Monetag to distribute malware like the Lumma info-stealer effectively.
For instance, as of 2023, about 70% of Google’s revenue comes from advertisements, highlighting the critical role of ad networks in the digital landscape.
However, this lucrative environment also attracts malicious actors, as seen in the recent deceptive campaigns that utilize advanced tricks to obscure their intent.
These trends indicate a growing challenge in recognizing and combating the infiltration of malware through legitimate advertising channels, emphasizing the need for heightened awareness and improved security measures on your part.
Mechanisms of Deception
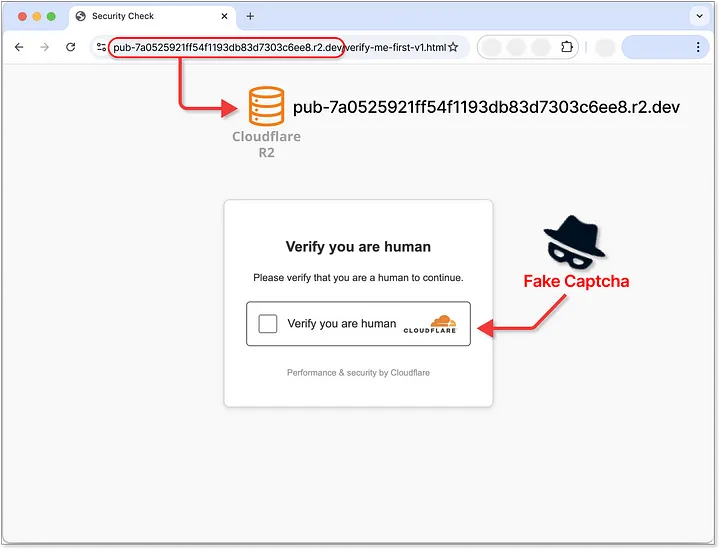
You may encounter deceptive fake captcha pages that appear legitimate while tricking you into installing infostealer malware.
These phishing tactics exploit familiar interfaces to manipulate your actions, often requiring just a few clicks on benign websites.
By obscuring their malicious intent beneath the guise of verifying human identity, threat actors successfully bypass defenses and target unsuspecting individuals, leading to the potential loss of sensitive information and financial assets.
Technical Breakdown of the Malware
The breakdown of the malware reveals an intricate scheme designed to exploit your trust.
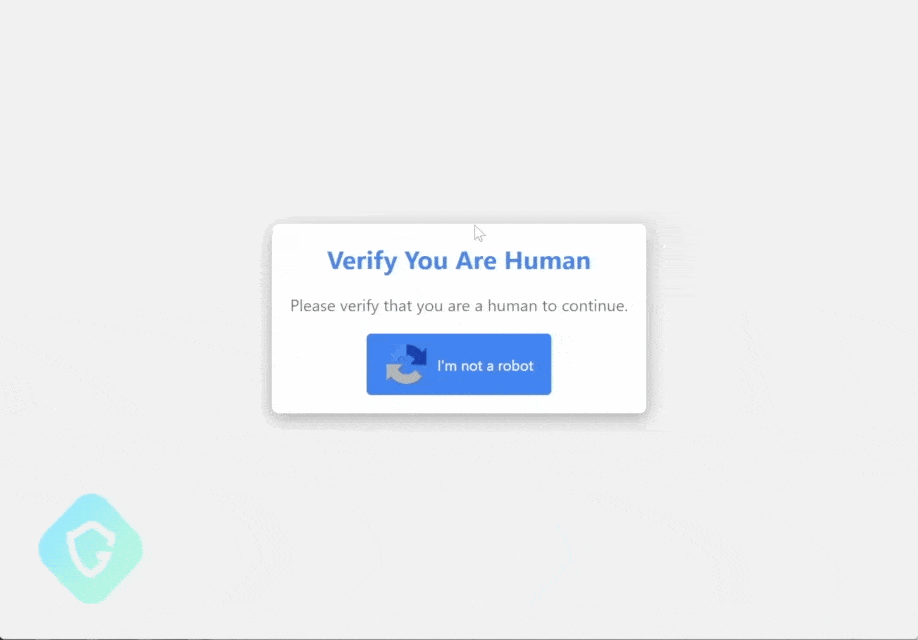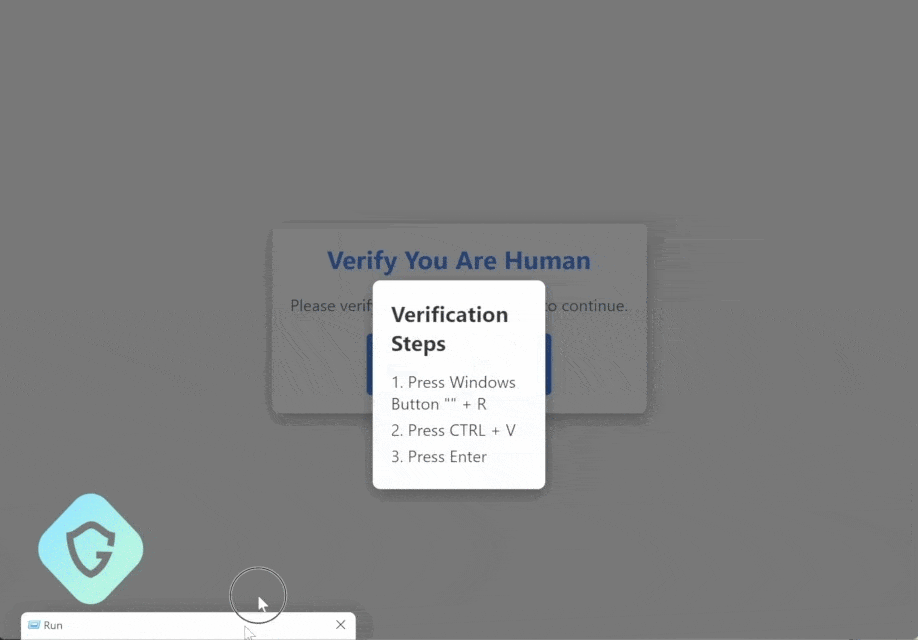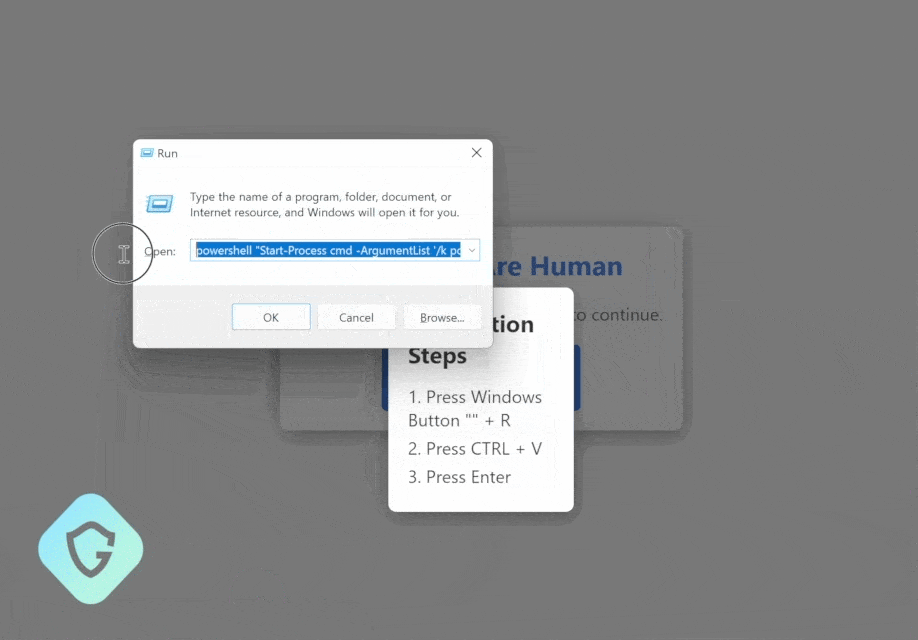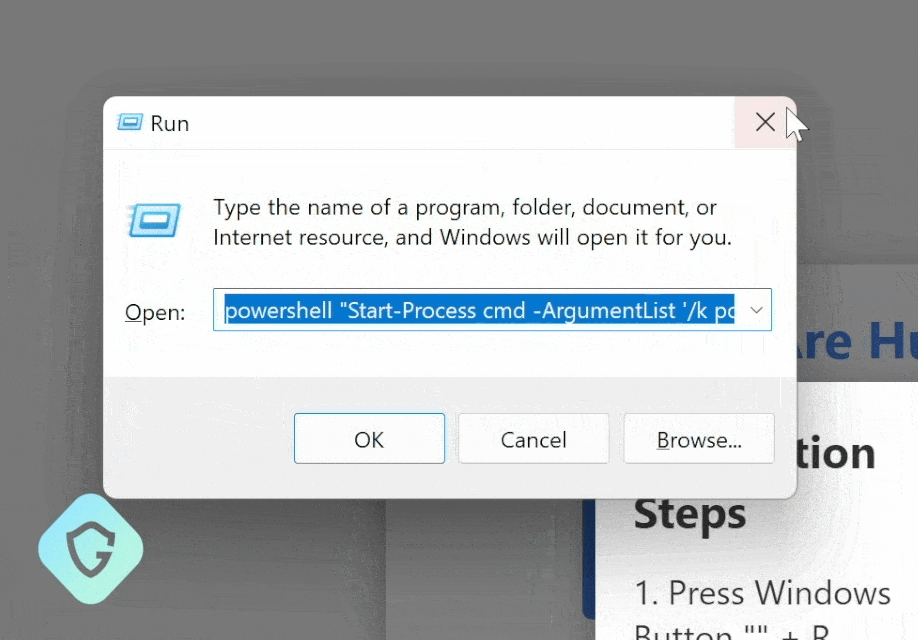
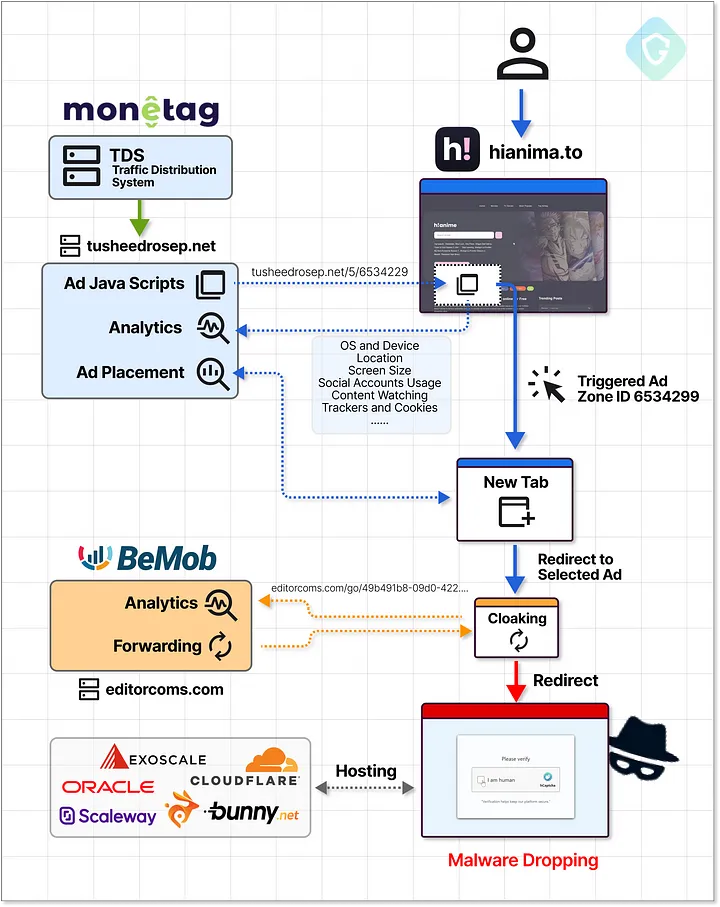
The Lumma info-stealer malware is delivered via a seemingly harmless captcha page, which you might unknowingly interact with while browsing.
By executing a malicious PowerShell command embedded within these pages, your sensitive credentials, from social media to banking information, are at risk.
With over 1 million daily ad impressions generated from around 3,000 publisher sites, the scale of this campaign poses significant threats to countless internet users.
Campaign analysis underscores the intricacy of the techniques involved. The malware’s execution relies on cleverly crafted scripts that prompt you to unwittingly run harmful commands.
From initial redirection through misleading ads to the final PowerShell execution, every step is designed to maintain invisibility and evade security measures.
As the campaign adapts with varying obfuscation methods and design updates, the risk to your personal information escalates, illustrating the importance of vigilance while navigating online spaces.
Keep your defenses strong to avoid falling victim to such deceptive tactics.
Infrastructure and Responsibilities
Assuming that you understand the intricate web of digital advertising, it’s necessary to recognize the role ad networks play in both distribution and accountability.
These networks, acting as intermediaries between advertisers and publishers, bear the responsibility for the content they handle.
In the case of the fake captcha campaign, the lack of stringent monitoring allowed malicious ads to thrive, leaving unsuspecting users vulnerable to malware infections, highlighting the urgent need for more robust oversight in the ad tech industry.
Case Study: Monetag and PropellerAds
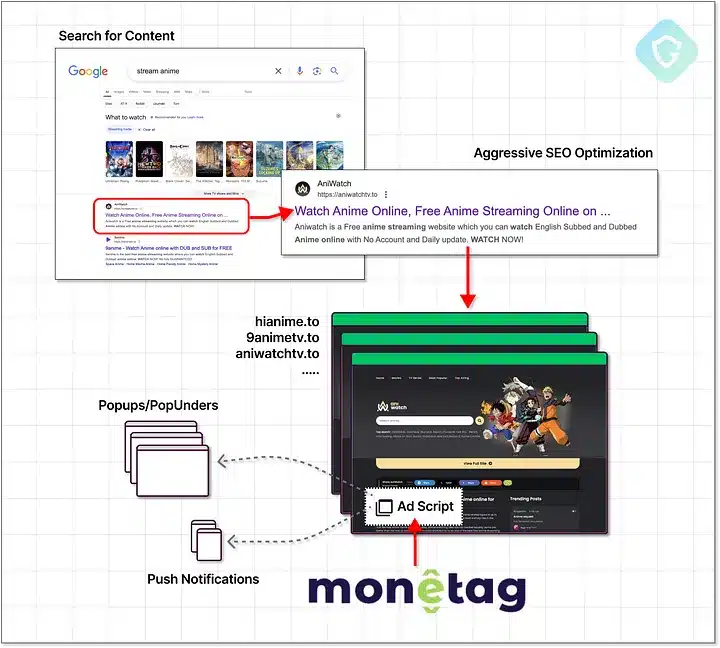
While exploring the ongoing malvertising threats, you may encounter Monetag, a subsidiary of PropellerAds, which has been linked to the spread of infostealer malware.
This ad network has proven to be a key player in facilitating the distribution of malicious content by providing a platform where cybercriminals can easily propagate deceptive ads, causing significant harm to internet users.
Monetag operates by integrating ad scripts into thousands of publisher websites, enabling a seamless flow of traffic to malicious sites. Their structure allows for rapid scaling of ad impressions—over 1 million daily, funneled through more than 3,000 domains.
The association with PropellerAds has raised concerns regarding the efficacy of ad content moderation, as issue after issue has arisen from their networks, ultimately putting your security at risk whenever you browse the internet.
Analysis of Redirect Chains
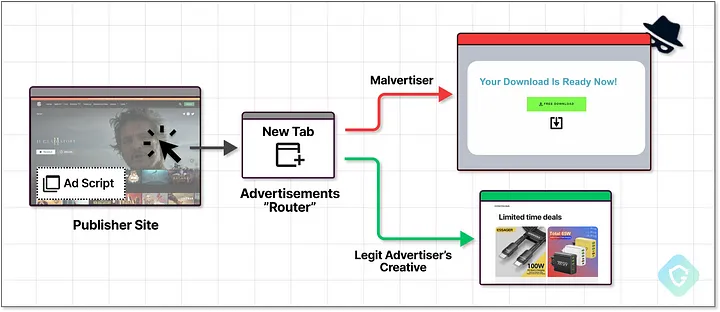
An effective aspect of the fake captcha campaign lies in its complex redirect chains. As you navigate seemingly benign sites, you may unwittingly click on ads leading to multiple redirects through various domains before reaching the malicious captcha page.
Our analysis identified over 3000 publisher sites funneling traffic through a single ad network, amplifying the reach of this 1 million daily ad impression campaign.
This intricate web obscures the malware’s true nature, luring countless users into a trap without realizing the danger.
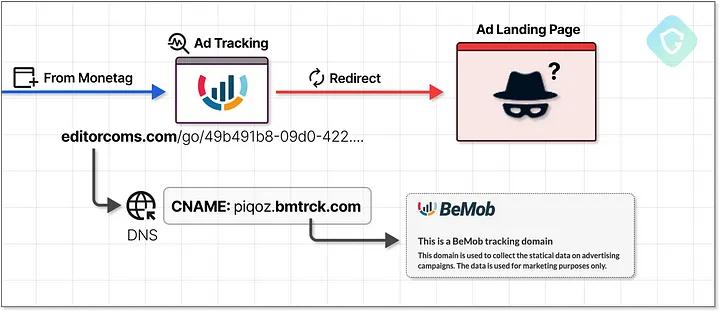
Cloaking Techniques Used by Threat Actors
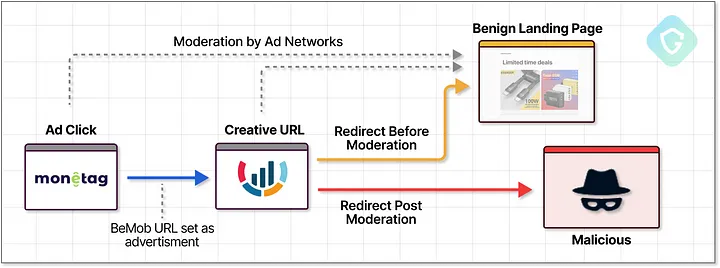
Redirect chains are further obscured by sophisticated cloaking techniques employed by threat actors.
You may encounter a seemingly legitimate URL that disguises the ultimate destination, making it challenging for ad networks to moderate content effectively.
For instance, these attackers utilize reputable ad-tracking services like BeMob to cloak their malicious URLs. Instead of linking directly to the harmful captcha page, they incorporate a benign BeMob URL within the ad network’s system.
This tactic not only conceals their intent but also complicates content moderation efforts, allowing their nefarious campaign to thrive amidst a vast ecosystem of legitimate ads.
By generating over 1 million daily ad impressions from 3000+ sites, the spread of infostealer malware becomes alarmingly effective, impacting unsuspecting users like you.

Scale of Victimization
Even while browsing innocuous websites, you are at risk of falling prey to the deceptive fake captcha campaign.
With over 1 million daily ad impressions and traffic directed through more than 3,000 content sites, thousands of unsuspecting users find themselves victimized by the stealthy Lumma info-stealer malware, compromising their online security.
Financial and Security Consequences
Financial losses can be devastating as you unknowingly surrender banking credentials and personal information to cybercriminals.
This malicious campaign not only endangers your financial assets but also exposes you to identity theft, making it difficult to regain control over your accounts.
Understanding the extent of these financial and security consequences is vital for protecting yourself.
With the Lumma malware targeting your sensitive data, a breach could lead to unauthorized transactions and account takeovers, leaving you vulnerable and facing long, stressful recovery processes.
As the numbers indicate, the scale of this campaign is alarming, and the repercussions can affect your personal finances and online presence for a long time.
Recommendations for Users
The implications of engaging with unfamiliar websites can lead to severe security risks.
To protect yourself, always verify the legitimacy of captcha prompts and avoid clicking on dubious ads. Consider using comprehensive security tools that enable real-time protection against threats like infostealer malware.
Regularly update your software and operating systems to close any vulnerabilities and back up your ‘personal’ data frequently to mitigate the impact of any potential breaches.
Industry Accountability and Reforms
If ad networks prioritized user safety and transparency, the frequency of malvertising incidents would decrease significantly.
It is crucial for you as a user to advocate for stricter regulations governing ad network operations to ensure they actively combat fraudulent activities.
When you demand accountability, it encourages companies to enforce higher standards in their advertising ecosystems, ultimately improving your online experience.
Recommendations for industry accountability include introducing stringent regulations for ad networks to monitor and analyze the content being disseminated.
Implementing mandatory verification processes for advertisers and increasing the penalties for malvertising can create a safer digital environment.
By remaining vigilant and pushing for reforms, you can help reduce the risk of deceptive ads like fake captchas while holding ad networks responsible for the content they allow on their platforms.
Together, these steps can lead to significant improvements in online security for everyone.





