Table of Contents
Cybersecurity experts have unearthed a sophisticated backdoor named Deadglyph, linked to the cyber espionage activities of a threat group known as Stealth Falcon.
This discovery sheds light on the evolving tactics used by malicious actors in the world of cyber espionage.
Key Takeaways to Deadglyph: New Advanced Backdoor Discovered:
- Deadglyph, an advanced backdoor, employs a unique architecture involving both a native x64 binary and a .NET assembly, setting it apart from typical malware.
- The use of distinct programming languages within Deadglyph is believed to be a deliberate strategy to obfuscate and complicate analysis.
- The backdoor is part of the arsenal of Stealth Falcon, a threat group known for targeting individuals and organizations in the Middle East, particularly activists and dissidents.
A Unique Backdoor Architecture
In a recent report, ESET cybersecurity researchers unveiled Deadglyph, an advanced backdoor that stands out due to its unconventional architecture. Unlike conventional malware, Deadglyph combines a native x64 binary with a .NET assembly.
This blend of programming languages is unusual and seems designed to impede analysis efforts, making it more challenging to dissect and debug.
Stealth Falcon’s Espionage History
Stealth Falcon, also known as FruityArmor, came into the spotlight in 2016 when Citizen Lab linked it to targeted spyware attacks in the Middle East. These attacks primarily targeted journalists, activists, and dissidents in the United Arab Emirates.
The group used spear-phishing tactics, employing malicious links in booby-trapped emails to deliver a custom implant capable of executing malicious commands.
Subsequently, in 2019, Reuters uncovered Project Raven, an operation involving former U.S. intelligence operatives working for the cybersecurity firm DarkMatter. Their mission was to spy on critics of the Arab monarchy.
Stealth Falcon and Project Raven share similarities in tactics and targets, suggesting they are the same group.
Prolific Zero-Day Exploitation
Stealth Falcon gained notoriety for its use of zero-day exploits in Windows, including CVE-2018-8611 and CVE-2019-0797. Mandiant reported that the group “used more zero-days than any other group” between 2016 and 2019.
Their tactics include employing Windows Background Intelligent Transfer Service (BITS) for command-and-control (C2) communications.
Deadglyph Emerges
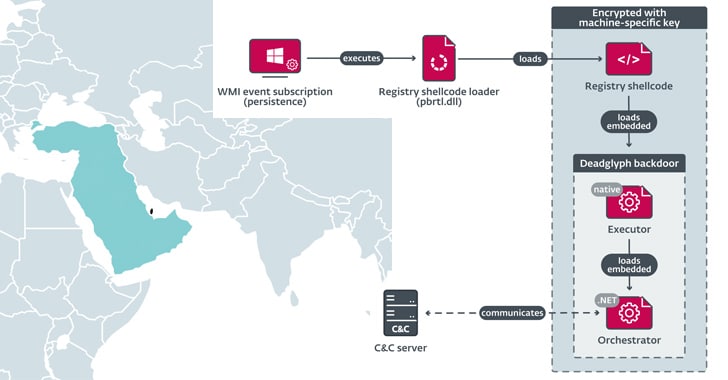
Deadglyph is the latest addition to Stealth Falcon’s cyber arsenal. ESET discovered it during the analysis of an intrusion at an undisclosed Middle Eastern government entity.
The exact delivery method remains unknown, but the initial component is a shellcode loader that extracts and launches Deadglyph’s native x64 module, known as the Executor.
The Executor, in turn, loads a .NET component called the Orchestrator, which communicates with the C2 server, awaiting instructions.
Sophisticated Evasion Tactics
Deadglyph employs multiple evasion techniques to avoid detection, including continuous monitoring of system processes and the use of randomized network patterns.
Additionally, the backdoor possesses the capability to uninstall itself, reducing the chances of detection.
Conclusion
The emergence of Deadglyph highlights the ever-evolving tactics used by threat actors in the realm of cyber espionage. Its distinctive architecture and association with Stealth Falcon underscore the persistent and evolving nature of cyber threats.
Organizations and individuals must remain vigilant and employ robust cybersecurity measures to defend against such advanced threats.
About ESET and Stealth Falcon: ESET is a prominent cybersecurity research firm known for its expertise in threat intelligence and analysis. Stealth Falcon, also recognized as FruityArmor, is a threat group with a history of conducting cyber espionage, particularly in the Middle East. Their activities have been closely monitored by cybersecurity researchers due to their high-profile targets and tactics.





