Table of Contents
New GPU Side-Channel Attack Risks Data Leakage: A recently published research paper reveals a concerning side-channel attack that threatens the security of modern GPU cards.
This news item explores the implications of this attack, how it was discovered, and the vulnerable GPUs from major manufacturers.
Key Takeaways to New GPU Side-Channel Attack Risks Data Leakage:
- GPU Vulnerability Unveiled: A new side-channel attack, known as “GPU.zip,” has been identified by researchers from four prominent American universities. This vulnerability can be exploited by malicious actors when a user visits a compromised website.
- Undocumented Compression Risk: The attack hinges on undocumented compression methods used by GPU vendors like Intel and AMD. These compressions occur even when software does not explicitly request them. Such compressions can lead to data-dependent memory traffic and cache utilization, opening avenues for side-channel analysis.
- Data Theft Potential: The attack’s significance lies in its potential to leak sensitive visual data bit by bit. By exploiting secret-dependent compressibility, attackers can exfiltrate data from HTTP/HTTPS requests and responses, reading information pixel by pixel. While the attack may require patience, it boasts high accuracy, making it a substantial threat.
Unmasking the GPU Side-Channel Vulnerability
A research paper authored by Yingchen Wang et. al. sheds light on this GPU side-channel attack. It is rooted in the little-known compression techniques employed by major GPU manufacturers such as Intel and AMD.
These compressions, utilized for memory bandwidth optimization and performance enhancement, can inadvertently expose data through side-channel analysis.
The Compression Conundrum
Compression techniques, while beneficial for performance, can become a double-edged sword.
The research paper underscores that compression-induced data-dependent DRAM traffic and cache utilization can be measured through side-channel analysis, providing attackers with the means to leak secrets.
Attacker’s Advantage
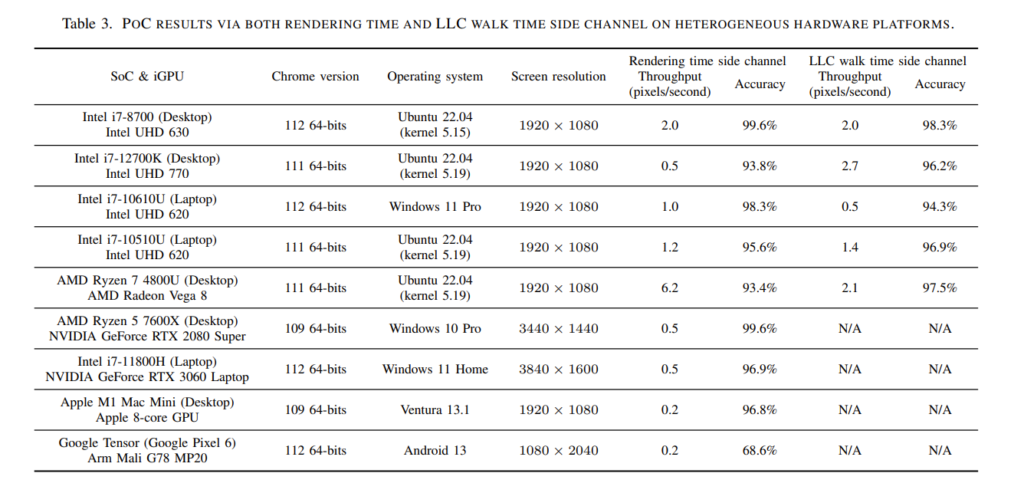
The attack’s real-world demonstration involved stealing usernames via an iframe on the Wikipedia site. Notably, the Ryzen side-channel attack yielded results within 30 minutes, while Intel GPUs took 215 minutes.
Despite the time investment, the attacks achieved impressively high accuracies of 97% and 98.3%, respectively.
Vigilance in a Vulnerable Landscape
As this GPU side-channel vulnerability comes to light, it underscores the need for heightened cybersecurity measures. The risk of data leakage, particularly sensitive visual data, poses a significant concern.
Users and organizations must remain vigilant and consider security updates to mitigate this emerging threat.
About the Researchers: The research paper detailing the GPU side-channel attack was authored by researchers from prominent American universities, including the University of Texas at Austin, Carnegie Mellon University, the University of Washington, and the University of Illinois. Their work highlights the critical need for addressing vulnerabilities in GPU technology to bolster cybersecurity measures.





