Table of Contents
Dallas Allocates $8.5 Million to Counter May Royal Ransomware Attack: The City of Dallas has earmarked $8.5 million to combat the Royal ransomware attack that struck in May 2023.
This news item dives into the details of the attack, its impact, and the measures taken to recover from it.
Key Takeaways Dallas Allocates $8.5 Million to Counter May Royal Ransomware Attack:
- Dallas allocates a substantial budget to recover from the Royal ransomware attack.
- The attack, which occurred in May 2023, disrupted vital city services and operations.
- The Royal ransomware gang, known for demanding hefty ransoms, is believed to have stolen sensitive data.
Uncovering the Ransomware Attack
In May 2023, the City of Dallas fell victim to a ransomware attack that severely affected its IT infrastructure.
To prevent the malware from spreading further within its network, the city authorities made the difficult decision to shut down impacted systems.
Impact on City Services
This cyberattack had widespread consequences, disrupting essential city services, including those provided by the police department. However, critical services like 911 remained operational.
The attack was significant enough to force the City to suspend jury trials and jury duty for several days in May.
The Royal Ransomware Group’s Threat
The Royal ransomware group is the perpetrator behind this attack. They threatened to expose stolen data unless the City met their ransom demands. The City’s response and investigation efforts have shed light on the nature of this incident.
The Royal Ransomware Attack Unveiled
According to a report titled “THE CITY OF DALLAS RANSOMWARE INCIDENT: MAY 2023” by the City of Dallas Department of Information & Technology Services ITS Risk Management, Security, and Compliance Services, the Royal ransomware gang gained access to the City’s infrastructure using a stolen domain service account.
Once inside, the group conducted reconnaissance and data exfiltration activities between April 7, 2023, and May 4, 2023.
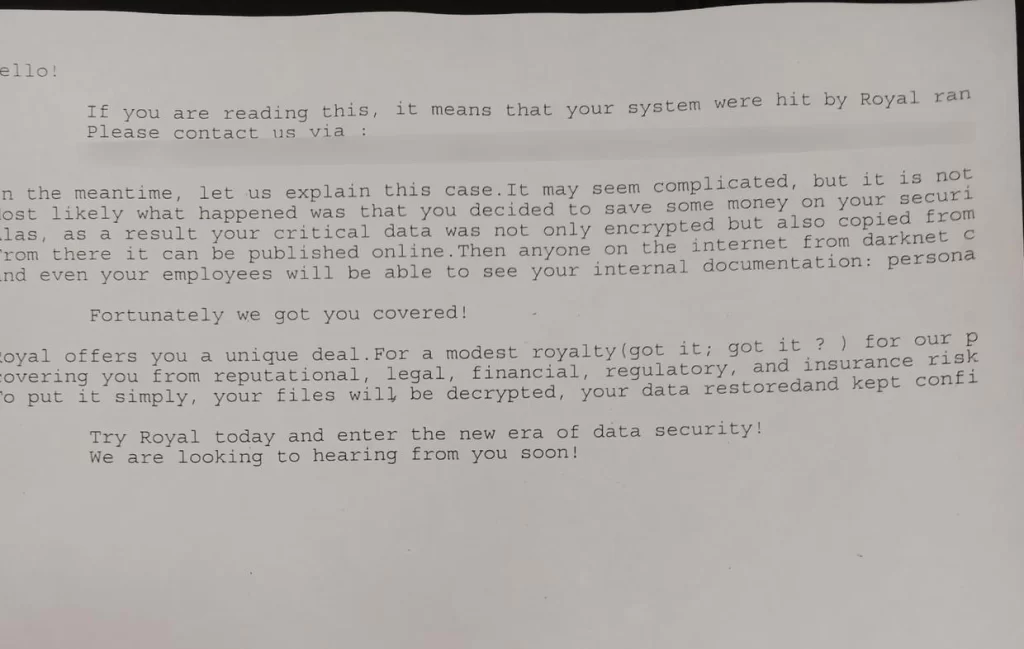
Stealing Data and Preparing for Ransomware
During this period, the Royal group stole data, amassing approximately 1.169 TB. They also made preparations for the ransomware attack, injecting command and control software and establishing beacons for this purpose.
The Ransomware Execution
On May 3, 2023, the Royal group executed the ransomware attack. City experts believe the attackers specifically targeted certain servers using legitimate Microsoft system administrative tools.
The City immediately initiated mitigation and recovery efforts, engaging external cybersecurity experts.
Restoring Services and Reporting Data Breach
The restoration process was a lengthy one, spanning over five weeks, from May 9 to June 13. As part of their obligations, the City reported the potential impact of the attack to the State of Texas Office of the Attorney General (TxOAG).
Personal information of thousands of residents, including sensitive data like social security and health information, was potentially exposed.
Mitigating the Attack
To counter the aftermath of this ransomware attack, the Dallas City Council has approved a substantial budget of $8.5 million.
About the Royal Ransomware Group
The Royal ransomware group, a human-operated threat, first surfaced in September 2022. This group is distinct in that it does not operate as a Ransomware-as-a-Service, maintaining a private status without a network of affiliates. Their ransom demands have been known to reach into the millions of dollars.
The group employs the post-exploitation tool Cobalt Strike for persistence and lateral movement. Their ransomware, written in C++, targets Windows systems and employs AES encryption, rendering data recovery challenging.
In March, the FBI and CISA released a joint Cybersecurity Advisory (CSA) detailing the tactics, techniques, and procedures (TTPs) and indicators of compromise (IOCs) associated with the Royal ransomware family.
The Royal Group has targeted critical infrastructure sectors, including manufacturing, communications, healthcare, public healthcare (HPH), and education, as reported by government experts.