Table of Contents
Chinese Hackers Target East Asian Semiconductor Firms with Cobalt Strike Attacks: In a recent cybersecurity development, Chinese hackers are zeroing in on semiconductor companies in East Asia.
These threat actors are using deceptive tactics, posing as Taiwan Semiconductor Manufacturing Company (TSMC) to deploy Cobalt Strike beacons.
Let’s delve into the details of this targeted campaign.
Key Takeaways to Chinese Hackers Target East Asian Semiconductor Firms with Cobalt Strike Attacks:
- Cobalt Strike Beacon Attacks: Chinese hackers are actively targeting semiconductor companies in East Asia, disguising themselves as TSMC, and using Cobalt Strike beacons for their attacks.
- HyperBro Backdoor: The attackers employ a backdoor called HyperBro as an entry point, enabling them to execute commercial attack simulation software and post-exploitation tactics.
- Multiple Attack Approaches: The threat actors are employing various techniques, including a previously undisclosed malware downloader, showcasing their adaptability and determination.
Understanding the Intrusion Set
Deceptive Tactics Unveiled
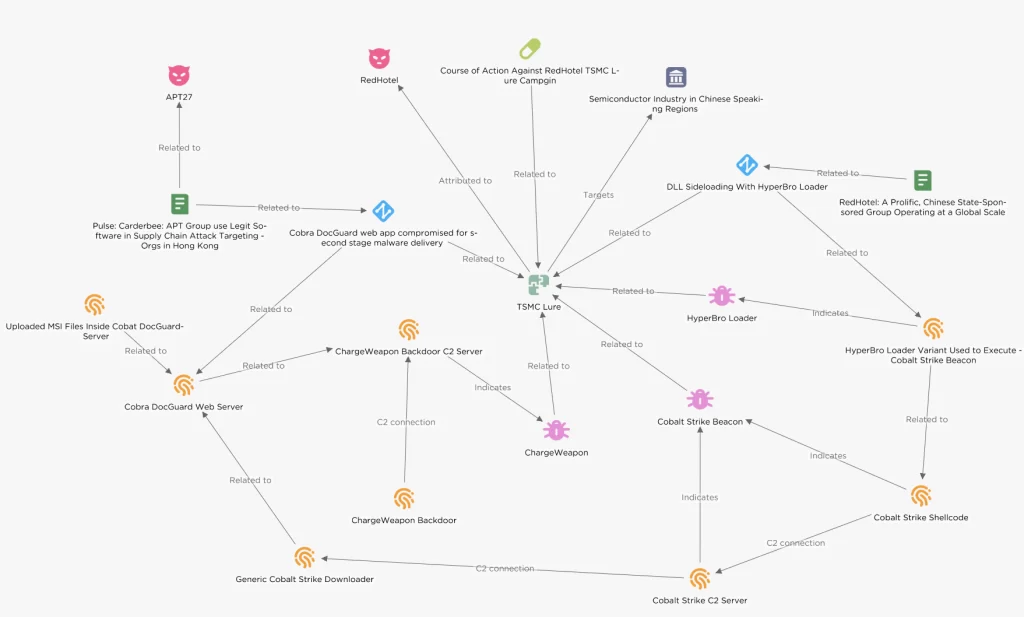
Recent observations reveal that threat actors have honed in on semiconductor companies in East Asia, masquerading as TSMC to launch their attacks. The modus operandi of this intrusion set involves using a backdoor known as HyperBro.
This backdoor serves as a conduit to introduce commercial attack simulation software and a post-exploitation toolkit into the target systems.
Tactics, Techniques, and Procedures (TTPs) Overlap
Notably, the tactics, techniques, and procedures (TTPs) employed in this campaign show similarities with activities previously attributed to People’s Republic of China (PRC)-backed cyber-espionage groups.
This suggests a coordinated and organized effort behind the attacks.
Versatility in Attack Methods
Interestingly, the attackers have shown adaptability by utilizing multiple approaches to infiltrate their targets. Besides HyperBro, they have deployed an undisclosed malware downloader to introduce Cobalt Strike.
This versatility underscores their determination to breach high-value targets.
Attribution to China-Linked Threat Actor
The Dutch cybersecurity firm, EclecticIQ, attributes this campaign to a China-linked threat actor, primarily based on their use of HyperBro.
This backdoor has historically been associated with a threat actor known as Lucky Mouse, which is also identified as APT27, Budworm, and Emissary Panda.
Tactical Overlaps and Chinese Connections
Further analysis reveals tactical overlaps between the group behind these attacks and another cluster tracked by RecordedFuture, known as RedHotel.
Additionally, these activities intersect with a hacking crew called Earth Lusca.
The use of a likely compromised Cobra DocGuard web server with Chinese connections adds another layer to this complex cyber campaign.
The HyperBro Loader and Cobalt Strike Connection
Loader Execution and Cobalt Strike Deployment
The HyperBro loader variant leverages a digitally signed CyberArk binary for DLL-side loading, ultimately leading to the execution of a Cobalt Strike beacon. This beacon serves as a bridgehead for the attackers.
Discovery of Malware Downloader
EclecticIQ analysts uncovered an undocumented malware downloader used in this campaign. This downloader utilizes PowerShell’s BitsTransfer module to fetch malicious binaries from a potentially compromised Cobra DocGuard server.
Malware Downloader’s Shellcode Execution
The malware downloader employs a DLL Side-Loading technique using a signed McAfee binary, mcods.exe, to run the Cobalt Strike shellcode. This shellcode shares the same Cobalt Strike Command and Control (C2) server address as the HyperBro loader variant.
The Role of ChargeWeapon
ChargeWeapon’s Functionality
One of the significant tools employed in these attacks is a Go-based implant named ChargeWeapon.
This implant is designed to establish remote access and send device and network information from compromised hosts to an attacker-controlled command-and-control server. The implications of such access can be severe.
Trojanized Software and Social Engineering
These attacks involve the use of trojanized versions of software, such as EsafeNet’s Cobra DocGuard encryption software.
This tactic has also been linked to the deployment of PlugX. Social engineering techniques, including a TSMC-themed PDF document, are used to initiate infections subtly.
Data Transmission and Reconnaissance
ChargeWeapon is designed to establish remote access to compromised hosts and transmit device and network information to an attacker-controlled C2 server.
The information collected serves as a foundation for initial reconnaissance against infected hosts.
Anti-Malware Evasion Techniques
To avoid detection, ChargeWeapon employs base64 encoding for obfuscation, making it harder for anti-malware solutions to identify the threat.
Operational Overlaps and Attribution
Likely State-Sponsored Attribution
EclecticIQ analysts have a high degree of confidence that this campaign, including the HyperBro loader, malware downloader, and ChargeWeapon, is likely operated and developed by a PRC-backed nation-state threat actor.
This conclusion is drawn based on victimology, infrastructure, malware code analysis, and similarities with previously reported activities.
Parallels with Recorded Future’s Analysis
The research findings share striking similarities with Recorded Future’s analysis of a Chinese state-sponsored group called RedHotel. Commonalities include the PDB file path, the use of Cobalt Strike, customized jQuery Malleable C2 profiles, and the DLL side-loading technique.
Evasion Techniques and International Implications
Firewall Evasion Tactics
A noteworthy aspect of this campaign is the disguising of the Cobalt Strike beacon’s command-and-control server address as a legitimate jQuery Content Delivery Network (CDN).
This deceptive move is aimed at bypassing firewall defenses.
International Ramifications
These cyber activities have international ramifications. Belgium’s intelligence and security agency, the State Security Service (VSSE), is actively working to detect and combat potential spying and interference activities by Chinese entities, including Alibaba, at Liège cargo airport.
China’s multifaceted approach to influence decision-making processes is under scrutiny.
Detection and Prevention Strategies
Security Measures Against Cyber Threats
To counter threats like these, organizations should consider the following security measures:
- Monitor for DLL side-loading activities under the C:\ProgramData file path, particularly those involving mcods.exe and vfhost.exe on Windows endpoints.
- Implement application whitelisting to block unsigned executable (EXE) executions on Windows endpoints and monitor suspicious download attempts using PowerShell cmdlets like Start-BitsTransfer.
- Restrict the usage of Windows PowerShell cmdlets for regular users or implement PowerShell module and script logging via Windows Group Policy.
- Block or monitor downloading attempts from specific infrastructure, such as AS-CHOOPA (Vultr) and Kaopu Cloud HK, which were consistently used by the threat actor.
Global Concerns and U.S. Department of Defense Report
Broad Cyber Espionage Threat
A recent report from the U.S. Department of Defense describes China as posing a pervasive cyber espionage threat.
The report highlights China’s engagement in prolonged campaigns of espionage, theft, and compromise, especially against critical infrastructure like the Defense Industrial Base (DIB).
Conclusion
The cyber landscape is ever-evolving, and the recent targeting of semiconductor firms in East Asia by Chinese hackers showcases the need for robust cybersecurity measures. Understanding their tactics and staying vigilant is crucial in today’s interconnected world.




