Table of Contents
Cybercriminals are stepping up their game with the Cloudflare Tunnel Hides GammaDrop Malware strategy. A new report reveals that the Russian-linked hacking group Gamaredon, also called BlueAlpha, is leveraging Cloudflare Tunnels and DNS fast-flux techniques to conceal its malware staging infrastructure.
This tactic enables the delivery of GammaDrop, a sophisticated malware, to unsuspecting victims in Ukraine and NATO countries.
Key Takeaway to Cloudflare Tunnel Hiding GammaDrop Malware:
- Cloudflare Tunnel Hides GammaDrop Malware: Gamaredon is using Cloudflare Tunnel Hides GammaDrop Malware techniques to bypass traditional security systems and target high-value organizations.
Who Is Behind These Attacks?
Gamaredon, also known by aliases like BlueAlpha and Primitive Bear, has been a significant player in cybercrime since 2014.
Believed to be affiliated with Russia’s Federal Security Service (FSB), this group specializes in spear-phishing campaigns to compromise government entities and critical infrastructure.
Their recent focus has been on Ukrainian organizations and NATO countries such as Latvia, Lithuania, and Poland. Gamaredon’s tactics have grown bolder, using tools like Cloudflare Tunnels to evade detection while distributing GammaDrop malware.
What Is GammaDrop Malware?
GammaDrop is a powerful malware used to compromise devices, steal sensitive data, and spread further malware. It enters systems through phishing emails with malicious HTML attachments, leveraging a tactic known as HTML smuggling.
Here’s how it works:
| Step | Details |
|---|---|
| Initial Infection | Phishing email with an HTML attachment is sent to the victim. |
| HTML Smuggling | When opened, the HTML attachment executes JavaScript to drop a malicious file. |
| Payload Deployment | The dropped file delivers GammaDrop using Windows mshta.exe utility. |
| Further Compromise | GammaDrop downloads additional malware via a Cloudflare Tunnel-protected server. |
Techniques Used by Gamaredon
Gamaredon’s strategy stands out due to its clever use of legitimate services like Cloudflare and DNS fast-fluxing.
Cloudflare Tunnels
By using Cloudflare Tunnels, Gamaredon hides the origin of its staging servers. This makes it harder for security systems to trace and block the source of the attack.
DNS Fast-Fluxing
Fast-flux DNS changes the IP addresses linked to a domain rapidly, complicating the efforts of defenders trying to disrupt communications with command-and-control (C2) servers.
HTML Smuggling
This technique embeds malicious code directly in email attachments, bypassing network defenses that scan for harmful links or files.
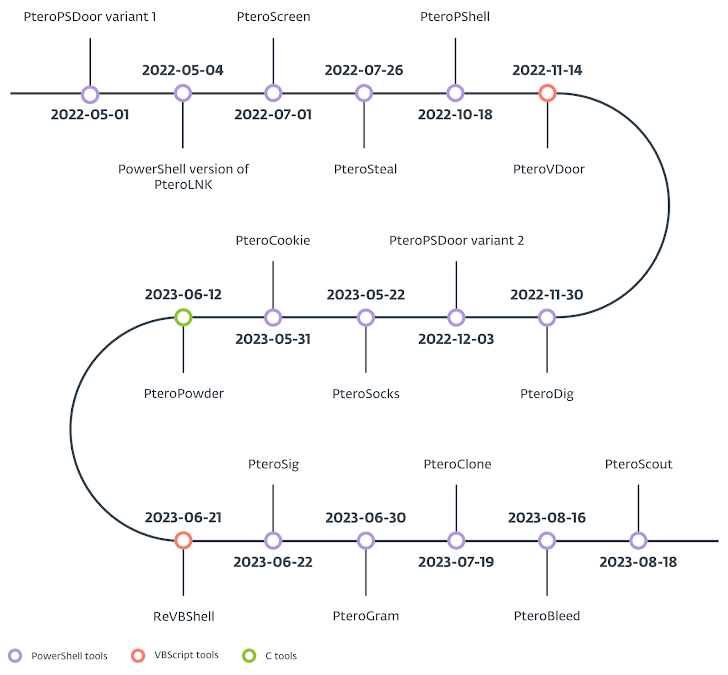
Malware Tools in Gamaredon’s Arsenal
Gamaredon uses a suite of tools designed for data theft, system compromise, and malware propagation.
| Tool Name | Purpose |
|---|---|
| PteroPSLoad | Downloads malicious payloads. |
| PteroCDrop | Delivers Visual Basic Script malware. |
| PteroLNK | Spreads malware via USB drives. |
| PteroSteal | Extracts saved browser credentials. |
| PteroSig | Steals data from Signal messaging app. |
| PteroBleed | Steals information from web-based apps like Telegram and WhatsApp. |
These tools are updated frequently, ensuring they remain effective against security measures.
What Can Organizations Do to Protect Themselves?
Gamaredon’s evolving tactics mean traditional security measures are often not enough. Here’s how organizations can defend against these threats:
- Train Employees: Educate staff about phishing techniques and how to spot suspicious emails.
- Use Advanced Threat Detection: Invest in systems capable of detecting and mitigating fast-flux DNS and malicious tunnels.
- Update Security Protocols: Regularly review and update software to patch vulnerabilities.
- Monitor Traffic: Look for unusual patterns that could indicate malicious activity.
For example, in 2022, a similar group used HTML smuggling to target financial institutions. Companies that implemented endpoint detection and response (EDR) systems were able to thwart these attacks successfully.
Conclusion
The Cloudflare Tunnel Hides GammaDrop Malware approach highlights how cybercriminals adapt to bypass defenses. Gamaredon’s tactics, such as fast-flux DNS and HTML smuggling, are a wake-up call for organizations to prioritize cybersecurity. Staying informed and proactive is essential to counter these evolving threats.
For in-depth insights on Gamaredon and its tools, check Recorded Future’s detailed analysis.
About Gamaredon (BlueAlpha)
Gamaredon, also known as BlueAlpha, is a hacking group linked to Russia’s FSB. Since 2014, the group has focused on targeting Ukrainian entities and NATO countries with malware attacks. Their tactics often involve spear-phishing and the use of legitimate tools to evade detection.
FAQ
What is GammaDrop malware?
GammaDrop is malware delivered via Cloudflare Tunnels, designed to steal data and deploy additional payloads.
How does Gamaredon hide its operations?
The group uses Cloudflare Tunnels and fast-flux DNS to obscure its malware infrastructure.
What is HTML smuggling?
HTML smuggling embeds malicious code in email attachments to bypass traditional network defenses.
Who are Gamaredon’s primary targets?
The group primarily targets Ukrainian organizations and NATO countries like Latvia, Lithuania, and Poland.
How can I protect my organization?
Implement advanced threat detection, train employees, and regularly update your security systems.





