Table of Contents
AtlasCross: Red Cross-Themed Phishing Unleashes New Backdoors: A recently discovered threat actor, AtlasCross, is employing sophisticated Red Cross-themed phishing tactics to disseminate two previously unidentified backdoors known as DangerAds and AtlasAgent.
This news item reveals the tactics and technical prowess of AtlasCross, shedding light on their targeted and persistent approach.
Key Takeaways to AtlasCross – Red Cross-Themed Phishing Unleashes New Backdoors:
- AtlasCross Emerges: A new threat actor, AtlasCross, has come to light, showcasing advanced technical skills and a methodical approach to cyberattacks.
- Red Cross-Themed Phishing: The attackers employ Red Cross-themed phishing lures to initiate their campaigns. Victims are enticed by a seemingly legitimate blood donation drive from the American Red Cross.
- DangerAds and AtlasAgent Backdoors: AtlasCross employs two backdoors, DangerAds and AtlasAgent, to infiltrate and compromise targeted systems. These backdoors exhibit evasive features to avoid detection by security tools.
AtlasCross Unveiled: A New Threat Actor
The emergence of AtlasCross has raised concerns in the cybersecurity community due to its demonstrated technical proficiency and deliberate approach to targeted attacks.
This actor’s modus operandi is characterized by precision and caution.
Red Cross-themed phishing Lures
AtlasCross initiates its attacks through Red Cross-themed phishing lures. These deceptive tactics involve masquerading as the American Red Cross, often centering around a supposed blood donation drive.
Victims are enticed to engage with malicious content, unaware of the impending threat.
DangerAds and AtlasAgent Backdoors
Upon interaction with the phishing lure, victims unwittingly trigger a macro-laden Microsoft document. This document serves as the entry point for AtlasCross’s intrusion. It facilitates the installation of two distinctive backdoors: DangerAds and AtlasAgent.
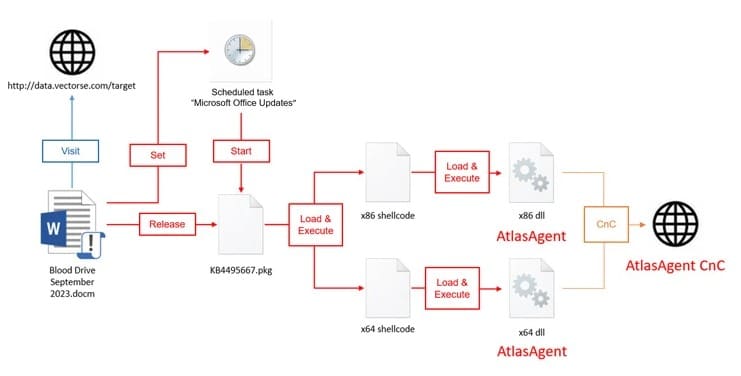
DangerAds operates as a loader, executing shellcode that eventually leads to the deployment of AtlasAgent. This C++ malware is equipped with multifaceted capabilities, including system data gathering, shellcode operations, command execution for reverse shell access, and code injection into specified processes.
Evasive Measures
AtlasAgent and DangerAds are designed with evasive features, making them challenging to detect by conventional security tools. This evasion strategy enhances their ability to infiltrate and compromise target systems.
The Enigma of AtlasCross
Despite extensive investigation, the true identity and motives of AtlasCross remain elusive. While their scope of activity appears limited to targeted attacks within specific network domains, their attack methods exhibit a high degree of sophistication and maturity.
Conclusion
The emergence of AtlasCross as a threat actor underscores the ever-evolving landscape of cybersecurity threats. Their use of Red Cross-themed phishing lures and the deployment of DangerAds and AtlasAgent backdoors highlight the need for heightened vigilance in the face of advanced and targeted cyberattacks.
Organizations and individuals must remain proactive in their security measures to mitigate such threats effectively.
About AtlasCross: AtlasCross, the newly identified threat actor, maintains an air of mystery surrounding its true identity and motives. While their current activities are relatively contained, their advanced attack techniques warrant ongoing attention and investigation from the cybersecurity community.





