Table of Contents
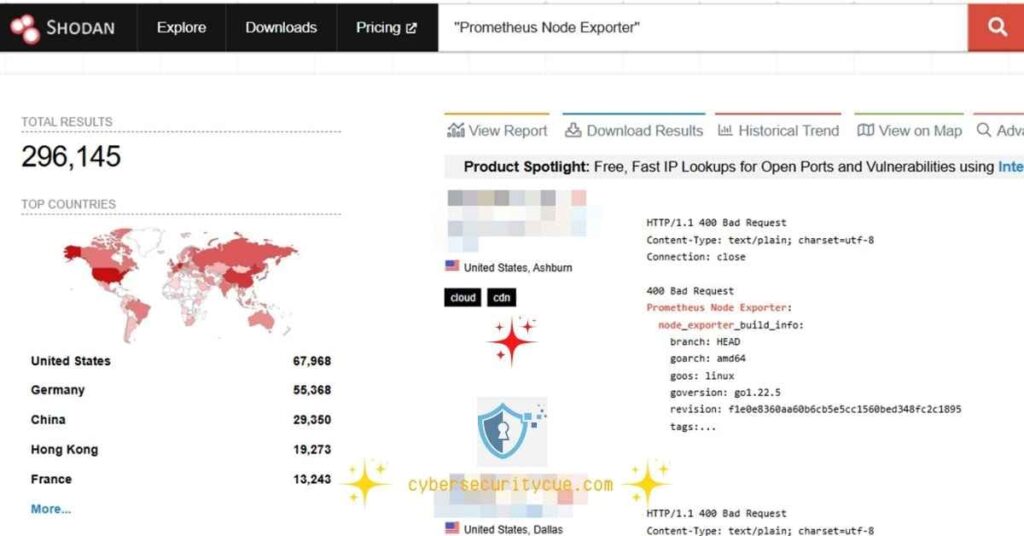
Did you know that over 300,000 Prometheus servers and exporters are vulnerable to attacks? This alarming Prometheus Servers vulnerable to cyberattacks discovery reveals how poor configuration and security lapses are exposing organizations to risks like data theft, denial-of-service (DoS) attacks, and remote code execution (RCE).
Prometheus, a popular monitoring and alerting toolkit, has become a double-edged sword for businesses relying on it to oversee their systems.
Key Takeaway to Prometheus Servers Vulnerable to Cyberattacks:
- Prometheus Servers Vulnerable to Cyberattacks: Exposing Prometheus servers to the public internet without proper security measures is a significant threat to organizational safety.
The Growing Threat to Prometheus Servers
Recent research has highlighted a staggering figure, more than 336,000 Prometheus servers and exporters are publicly accessible, making them easy targets for cybercriminals.
These servers often lack authentication, allowing attackers to exploit vulnerabilities for malicious purposes.
What Makes Prometheus Vulnerable?
Prometheus servers are often deployed with minimal security settings, leading to:
| Risk | Description |
|---|---|
| Information Disclosure | Attackers can access sensitive data like credentials, API keys, and internal metrics. |
| Denial of Service (DoS) | Misconfigured debugging endpoints (/debug/pprof) allow attackers to overwhelm servers. |
| Remote Code Execution | RepoJacking vulnerabilities let attackers inject malicious code through compromised exporters. |
Real-World Example: Skoda’s Prometheus Exposure
In one case, researchers discovered an unauthenticated Prometheus instance linked to Skoda, a major European car manufacturer. This instance revealed sensitive data such as Docker registries, internal API endpoints, and subdomains.
Attackers could have exploited this information to infiltrate Skoda’s systems. Fortunately, the issue was reported and promptly mitigated by Skoda’s security team.
Details of the Vulnerabilities
Information Disclosure
When Prometheus servers are exposed to the public, attackers can query metrics endpoints to extract sensitive information.
This includes passwords, tokens, and even internal backend data. Such disclosures provide attackers with a roadmap to infiltrate an organization’s systems.
Denial of Service (DoS) Attacks
Prometheus’ default debugging interface (/debug/pprof) is a potential weapon for attackers. By sending repeated requests to profiling endpoints, attackers can exhaust CPU and memory resources, causing system outages.
For instance, in a Kubernetes environment, this could lead to repeated pod crashes, disrupting the entire cluster.
RepoJacking Risks
RepoJacking is a supply chain attack where attackers hijack abandoned GitHub repositories to inject malicious code.
Researchers found several Prometheus exporters vulnerable to RepoJacking, including popular ones like the AWS Cost Exporter and Docker Hub Exporter.
Mitigation Steps
Protecting Prometheus servers requires a combination of technical safeguards and best practices:
| Action | Recommendation |
|---|---|
| Enable Authentication | Implement strong authentication to restrict access to Prometheus servers and endpoints. |
| Restrict Public Access | Deploy Prometheus behind firewalls or VPNs to minimize exposure. |
| Disable Debugging Endpoints | Disable or restrict access to /debug/pprof endpoints, especially in production environments. |
| Verify Open-Source Links | Regularly audit linked exporters and repositories to prevent RepoJacking. |
| Implement Resource Limits | Set limits on CPU and memory usage to prevent DoS attacks from overwhelming your servers. |
Rounding Up
The revelation that over 300,000 Prometheus servers are vulnerable to attacks underscores the need for immediate action. Organizations using Prometheus must prioritize security by adopting robust configurations and practices.
Cyber threats evolve daily, and leaving systems exposed is an open invitation to attackers. Take steps today to protect your Prometheus.io servers and secure your infrastructure.
FAQs
What is Prometheus used for?
Prometheus is an open-source tool for monitoring systems and alerting users about performance issues. It collects metrics, stores them, and allows users to analyze data in real time.
Why are Prometheus servers vulnerable?
Poor security practices, such as leaving servers exposed without authentication, make them easy targets for cyberattacks.
What is RepoJacking?
RepoJacking is a supply chain attack where attackers take control of abandoned GitHub repositories to inject malicious code.
How can I secure my Prometheus deployment?
Implement authentication, limit public access, monitor debugging endpoints, and audit linked repositories for potential risks.
Where can I learn more about Prometheus security?
Visit the Prometheus documentation for detailed security guidelines.





