Table of Contents
Have you ever wondered how cybercriminals exploit hacked devices to fuel their operations? Socks5Systemz botnet powers Proxy.AM, a controversial proxy service, which is using over 85,000 compromised systems worldwide.
This sophisticated botnet has silently operated under the radar for years, providing anonymity for illegal activities. Investigation reveals how this malware evolved, the scale of its impact, and the implications for cybersecurity.
Key Takeaway
- How Socks5Systemz Botnet Powers Proxy.AM: A cyber threat leveraging over 85,000 hacked devices to run an illicit proxy network.
Unveiling Socks5Systemz: The Origins
The Socks5Systemz botnet first surfaced on underground forums in 2013 but gained traction only in recent years. This malware converts hacked devices into proxy exit nodes, allowing threat actors to mask their online activity.
Initially part of larger malware campaigns like Andromeda and Smokeloader, Socks5Systemz operated unnoticed by many researchers until late 2023.
Timeline of Socks5Systemz Development:
| Year | Milestone |
|---|---|
| 2013 | First mentioned in Russian cybercrime forums |
| 2017 | Integrated as a SOCKS5 proxy module for Andromeda and Trickbot |
| 2023 | Standalone version gains widespread attention |
| 2024 | Estimated 85,000-100,000 active bots globally |
How Socks5Systemz Botnet Powers Proxy.AM
The botnet enables Proxy.AM to offer “elite, private, and anonymous” proxy services to its customers. According to Bitsight TRACE’s research, Proxy.AM boasts over 300,000 proxies and earns revenue through subscription packages ranging from $90 to $700 per month.
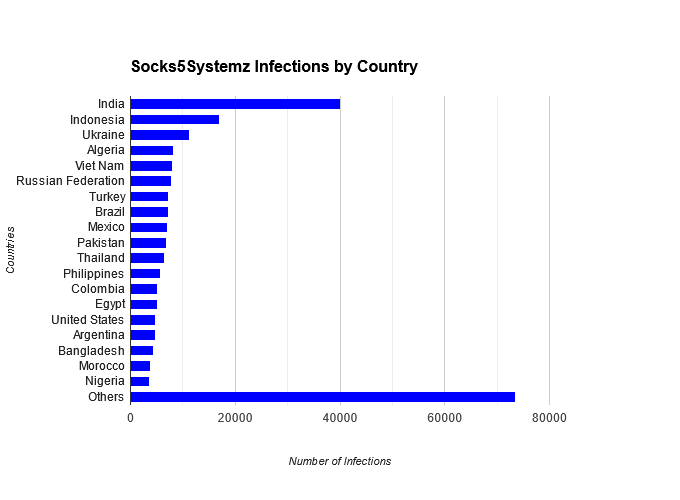
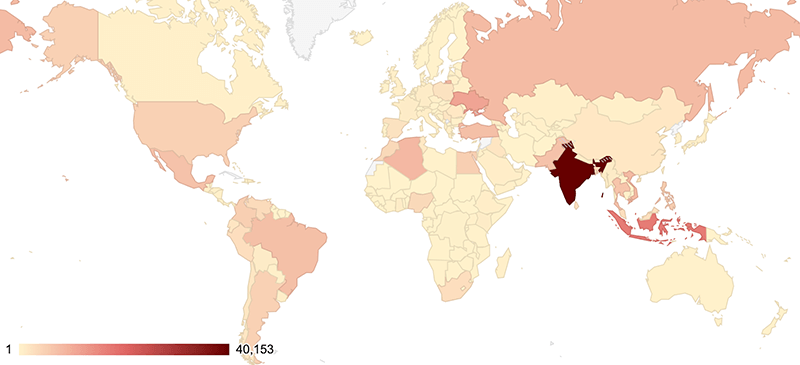
This massive network thrives by compromising devices in countries such as India, Indonesia, and Ukraine.
Here’s a breakdown of the most affected regions:
| Country | Infections |
|---|---|
| India | 40,153 |
| Indonesia | 17,027 |
| Ukraine | 11,178 |
| Algeria | 8,255 |
| Vietnam | 8047 |
| Russian Federation | 7826 |
| Turkey | 7288 |
| Brazil | 7224 |
| Mexico | 6987 |
| Pakistan | 6802 |
| Thailand | 6452 |
| Philippines | 5664 |
| Colombia | 5165 |
| Egypt | 5164 |
| United States | 4,784 |
| Argentina | 4756 |
| Bangladesh | 4432 |
| Morocco | 3758 |
| Nigeria | 3625 |
| Others | 73573 |
The top 10 most affected countries are, in order, India, Brazil, Colombia, South Africa, Bangladesh, Argentina, Angola, United States, Suriname, and Nigeria.
Why Has Socks5Systemz Remained Under the Radar?
Experts believe its stealth is due to its integration within other malware families. By operating as a proxy module for Andromeda and Smokeloader, Socks5Systemz avoided direct detection.
Its resurgence as a standalone malware in 2023 signals a shift in the cybercrime ecosystem.
Malware Evolution and Infrastructure Updates
Recent changes in Socks5Systemz include:
- Expanded Infrastructure: 26 servers spread across Europe.
- Advanced Malware Obfuscation: Harder to detect and analyze.
- Improved Protocols: Updates in communication and encryption methods.
Despite these upgrades, its core functionality remains the same: turning hacked devices into proxy nodes.
Proxy.AM’s Role in Cybercrime
Proxy.AM markets itself as a legitimate service, but its reliance on the Socks5Systemz botnet reveals its dark underpinnings.
By exploiting a vast network of infected devices, the service aids cybercriminals in anonymizing activities, including fraud and ransomware.
![How Socks5Systemz Botnet Powers Proxy.AM with 85,000+ Devices 24 Relationship graph between bddns[.]cc, proxy[.]am and 109.235.81[.]104_ SOURCE - bitsight.com](https://cybersecuritycue.com/wp-content/uploads/2024/12/Relationship-graph-between-bddns.cc-proxy.am-and-109.235.81.104_.png)
Rounding Up
The revelation that Socks5Systemz botnet powers Proxy.AM highlights the evolving nature of cyber threats. As malware becomes more sophisticated, security experts and organizations must remain vigilant.
Bitsight TRACE and other cybersecurity entities play a vital role in uncovering these operations and mitigating their impact.
By shedding light on this cybercrime operation, we aim to raise awareness about the importance of proactive cybersecurity measures. Stay informed and protected!
About Bitsight TRACE
Bitsight TRACE is a leading cybersecurity research and intelligence platform. They specialize in uncovering hidden cyber threats and providing actionable insights to protect organizations worldwide.
FAQ: How Socks5Systemz Botnet Powers Proxy.AM
What is Socks5Systemz?
A: Socks5Systemz is malware that converts hacked devices into proxy exit nodes for anonymity.
How does Proxy.AM use this botnet?
A: Proxy.AM leverages the compromised devices in the botnet to offer proxy services.
Why is this a cybersecurity concern?
A: The botnet enables criminals to mask malicious activities, increasing risks for individuals and organizations.
What countries are most affected?
A: India, Indonesia, and Ukraine are among the top countries with high infections.
How can individuals protect themselves?
A: Regularly update software, use strong passwords, and install reputable antivirus solutions.





