Table of Contents
When it comes to cyber warfare, few groups are as cunning as Turla. In a recent development, Turla exploits Pakistani hackers’ servers in an unprecedented cyber campaign, targeting Afghan and Indian entities.
Turla Exploits Pakistani Hackers Servers to Target South Asia
This Russia-linked hacking group took control of servers belonging to Storm-0156, a Pakistan-based hacking group, and turned them into tools for espionage.
The findings, shared by Lumen Technologies’ Black Lotus Labs and Microsoft Threat Intelligence, reveal just how advanced and adaptive Turla has become.
Key Takeaway to Turla Exploits Pakistani Hackers Servers:
- Turla’s ability to hijack another hacker group’s infrastructure highlights their sophisticated approach to evading detection and advancing their espionage goals.
What Happened? A Look at Turla’s Latest Tactics
Turla’s New Strategy: Hijacking Servers
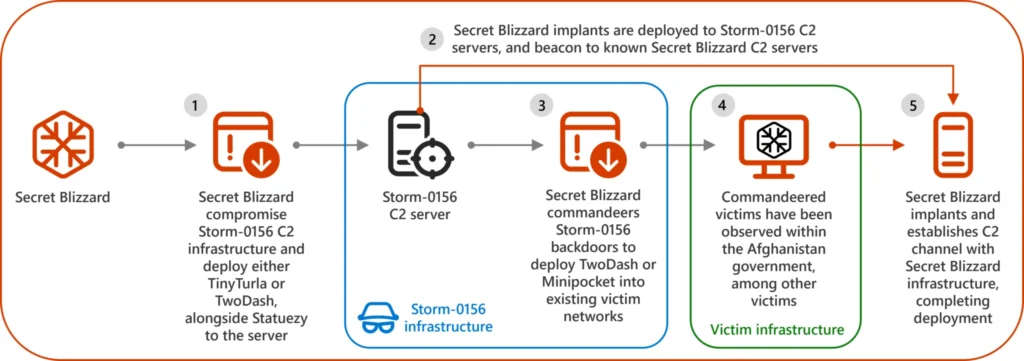
Turla, also known as Secret Blizzard, accessed Storm-0156’s command-and-control (C2) servers in December 2022. By mid-2023, they expanded control over multiple servers used by Storm-0156 to manage stolen data and coordinate attacks.
This wasn’t just opportunistic hacking but was calculated. Turla used their access to deploy their own malware, such as TwoDash and Statuezy, targeting Afghan government networks.
They also infiltrated Indian networks, focusing on servers hosting critical military and defense data.
What Tools Did Turla Use?
Turla deployed several advanced tools:
| Tool | Purpose |
|---|---|
| TwoDash | Downloader for additional malware payloads |
| Statuezy | Trojan for monitoring Windows clipboard activity |
| MiniPocket | Custom downloader for second-stage malware |
How Did Turla Compromise Storm-0156?
The exact method Turla used to infiltrate Storm-0156’s servers remains unclear, but they took full advantage of the situation. Once inside, they not only deployed their malware but also gained access to critical information about Storm-0156’s tools, targets, and stolen data.
This allowed Turla to expand its intelligence operations without directly targeting organizations, reducing their risk of being detected. For example, instead of launching attacks on Afghan entities themselves, Turla leveraged Storm-0156’s existing access to these networks.
Turla’s History of Hijacking Other Hackers
Previous Operations by Turla
This isn’t the first time Turla has piggybacked on another hacker group. In 2019, they exploited an Iranian hacker group’s infrastructure to deploy their own tools. Similarly, in 2023, Turla used infrastructure tied to the Tomiris backdoor to carry out attacks in Kazakhstan.
These tactics not only obscure Turla’s involvement but also complicate attribution efforts, making it harder for researchers to identify who’s responsible.
Why This Approach Matters
Hijacking another hacker’s operations offers two key advantages:
- Reduced Effort: Turla capitalizes on the groundwork already laid by other groups.
- Increased Anonymity: Attribution becomes murky, as the original hacker group appears responsible for the activity.
What Does This Mean for Cybersecurity?
Global Implications
This campaign highlights the growing complexity of cyber espionage. With groups like Turla adopting unconventional methods, cybersecurity experts face an uphill battle in detecting and attributing attacks.
Lessons Learned
- Advanced Threats Require Advanced Defense: Organizations must constantly update their defenses to stay ahead of these tactics.
- Collaboration Is Key: International cooperation, like the partnerships between Black Lotus Labs and Microsoft, is crucial in identifying and stopping such campaigns.
About Turla
Turla, also known as Secret Blizzard, is a Russia-linked hacking group active for nearly 30 years. Affiliated with the Russian Federal Security Service (FSB), Turla is notorious for targeting government, diplomatic, and military organizations worldwide.
Their toolset includes advanced malware like Snake, ComRAT, and Kazuar, making them one of the most sophisticated cyber-espionage groups.
Conclusion: A Wake-Up Call for Cybersecurity
The revelation that Turla exploits Pakistani hackers’ servers is a reminder of the ever-evolving nature of cyber threats. By hijacking another group’s infrastructure, Turla demonstrated their ability to outsmart traditional defenses and adapt to the changing cybersecurity landscape.
To stay ahead, organizations and governments must invest in robust security measures and foster global cooperation. As cybercriminals get smarter, so must we.
FAQs
Who is Turla?
Turla is a Russia-linked hacking group known for sophisticated cyber espionage campaigns targeting government and military organizations.
What is Storm-0156?
Storm-0156 is a Pakistan-based hacking group whose servers were hijacked by Turla for espionage operations.
What malware did Turla deploy in this campaign?
Turla used tools like TwoDash, Statuezy, and MiniPocket to infiltrate networks and collect data.
Why is Turla’s approach significant?
By hijacking another group’s infrastructure, Turla reduces their own risk while complicating attribution efforts.
How can organizations protect themselves?
Stay updated on cybersecurity trends, invest in advanced threat detection, and collaborate with international cybersecurity organizations.





