Table of Contents
Lazarus Group Targets Spanish Aerospace Firm via Meta Impersonation: The Lazarus Group, a North Korea-linked cyber espionage outfit, has launched a cyber attack against an aerospace company in Spain.
The threat actors posed as a recruiter from Meta (formerly Facebook) to deceive employees into opening malicious files, marking a significant development in their spear-phishing campaign.
Key Takeaways on Lazarus Group Targets Spanish Aerospace Firm via Meta Impersonation:
- Meta Recruiter Impersonation: Lazarus Group posed as Meta recruiters on LinkedIn to trick employees of a Spanish aerospace firm into downloading malicious files.
- Operation Dream Job: This attack is part of Operation Dream Job, a spear-phishing campaign designed to lure employees with promising job opportunities to initiate cyberattacks.
- Advanced Malware: The attackers deployed a sophisticated Windows malware called LightlessCan, showcasing an evolution from their previous tool, BLINDINGCAN.
Meta Impersonation and Cyber Espionage
The Lazarus Group, known for its cyber espionage activities linked to North Korea, has been implicated in a targeted attack on a Spanish aerospace company.
The attackers used a clever ruse by impersonating recruiters from Meta Platforms (formerly Facebook) to infiltrate the organization.
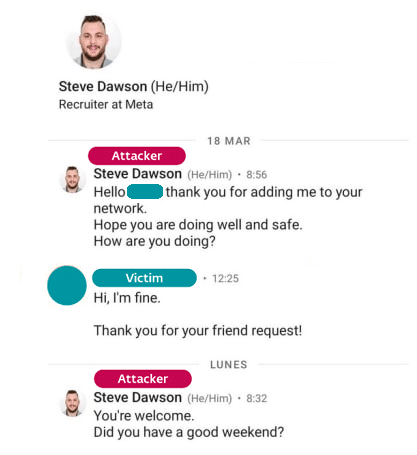
Operation Dream Job Spear-Phishing
This attack is part of Operation Dream Job, a long-standing spear-phishing campaign orchestrated by the Lazarus Group.
The campaign aims to entice employees of strategic interest organizations with enticing job opportunities, ultimately leading to the activation of malicious payloads.
Evolution of Attacks
Notably, Lazarus Group’s tactics have evolved. In a previous attack, the group used fake HSBC job offers to distribute a Linux backdoor named SimplexTea.
In this recent intrusion targeting Windows systems, their objective was to deploy an implant called LightlessCan.
LightlessCan: A Sophisticated Threat
The most concerning aspect of this attack is the use of LightlessCan. This malware represents a significant advancement in malicious capabilities compared to its predecessor, BLINDINGCAN.
LightlessCan is highly sophisticated and exhibits complex design and operation characteristics.
Attack Execution
The attack began with a LinkedIn message to the target, supposedly from a Meta recruiter. The victim was presented with coding challenges as part of a hiring process. To complete these challenges, the victim was encouraged to execute test files hosted on a third-party cloud storage platform.
These test files, named Quiz1.iso and Quiz2.iso, contained malicious binaries (Quiz1.exe and Quiz2.exe). When executed on a company-provided device, these files compromised the system, allowing the attackers to proceed.
Deployment of Malware
Once the system was compromised, the attackers introduced an HTTP(S) downloader known as NickelLoader. This downloader facilitated the deployment of various programs into the victim’s computer’s memory.
Notably, this included the LightlessCan remote access trojan and a variant of BLINDINGCAN called miniBlindingCan (also known as AIRDRY.V2).
LightlessCan’s Capabilities
LightlessCan is a powerful tool equipped with support for up to 68 distinct commands, with 43 of them currently implemented.
Its functions enable discreet execution within the RAT itself, enhancing stealthiness and making it more challenging to detect and analyze the attacker’s activities.
Strategic Guardrails
One distinctive feature of this campaign is the use of execution guardrails. These mechanisms prevent the payloads from being decrypted and run on any machine other than the intended victim’s, further enhancing the stealthiness of the attack.
Conclusion
The Lazarus Group’s use of Meta impersonation to target a Spanish aerospace firm highlights the group’s evolving tactics in cyber espionage.
The deployment of the sophisticated LightlessCan malware underscores the need for vigilance and robust cybersecurity measures to counter such threats.
About ESET:
ESET is a reputable cybersecurity company known for its expertise in threat research and analysis.





