Table of Contents
Ukrainian Military Targeted in Drone Manual Phishing Attack: Ukrainian military units are facing a phishing campaign designed to compromise their systems, with attackers using drone manuals as bait.
The cybercriminals deploy a Go-based open-source post-exploitation toolkit named Merlin as part of their strategy.
This scheme, monitored under the name STARK#VORTEX, capitalizes on the significance of drones in Ukrainian military operations.
Key Takeaways to Ukrainian Military Targeted in Drone Manual Phishing Attack:
- Phishing Campaign Aimed at Ukrainian Military: Ukrainian military organizations have become the focus of a phishing campaign utilizing drone manuals as deceptive documents.
- Merlin Toolkit Deployment: The attackers employ the Merlin toolkit, written in Go, to facilitate post-exploitation actions on compromised systems.
- Sophisticated Evasion Techniques: Despite the attack chain’s apparent simplicity, the threat actors employ complex tactics, techniques, and procedures (TTPs) and obfuscation methods to evade detection.
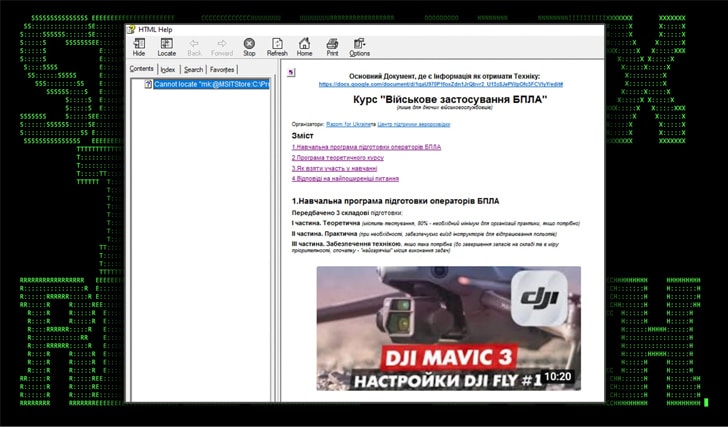
Phishing Lures with Drone Manuals
The attack initiates with a Microsoft Compiled HTML Help (CHM) file. When opened, this file executes malicious JavaScript embedded within an HTML page.
This JavaScript, in turn, triggers PowerShell code that connects to a remote server to obtain an obfuscated binary.
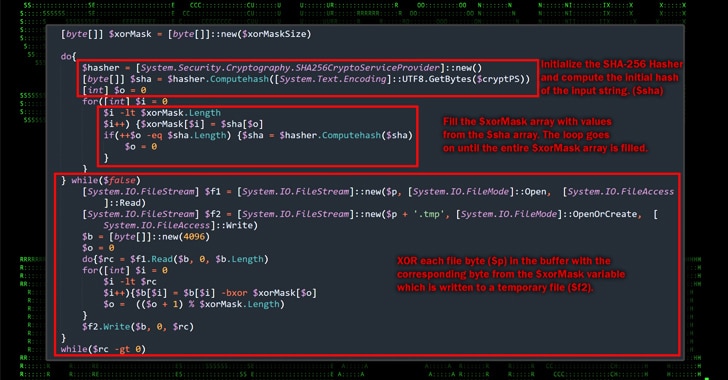
Merlin Agent Takes Control
The obfuscated binary retrieved from the remote server contains the Merlin Agent. This agent is configured to communicate with a command-and-control (C2) server, allowing the attackers to gain control over the compromised host.
The C2 server facilitates post-exploitation activities.
Evasion and Deception
While the attack appears straightforward, the threat actors employ intricate techniques to avoid detection. The attackers’ ability to conceal their activities is attributed to these sophisticated tactics and obfuscation methods.
Ukrainian Government Organizations in the Crosshairs
This is the first known instance of Ukrainian government entities being targeted using the Merlin toolkit. Previously, the Computer Emergency Response Team of Ukraine (CERT-UA) disclosed a similar campaign in August 2023, where CHM files were used to deceive users and infect systems with the open-source tool.
CERT-UA attributed the earlier intrusions to a threat actor identified as UAC-0154. The documents and files used in these attacks are adept at bypassing typical security defenses by masquerading as legitimate help-themed documents.
Conclusion
The phishing campaign’s use of drone manuals as bait highlights the evolving tactics of cybercriminals targeting military and government organizations. The ability to disguise malicious activity within seemingly innocuous documents underscores the need for robust cybersecurity measures and user vigilance in detecting such threats.
About Merlin Toolkit: The Merlin toolkit is a Go-based open-source post-exploitation tool used by threat actors to gain control over compromised systems. It facilitates various post-exploitation actions and is known for its flexibility and evasion capabilities.
About CERT-UA: The Computer Emergency Response Team of Ukraine (CERT-UA) is responsible for monitoring and responding to cybersecurity incidents in Ukraine. It plays a crucial role in identifying and mitigating cyber threats to the country’s critical infrastructure and government organizations.





