Table of Contents
Hotel Hackers Using Fake Booking.com Pages to Steal Guests’ Credit Cards: Security researchers have uncovered a sophisticated information-stealing campaign where cybercriminals infiltrate hotel and booking site systems to target customers’ financial data.
This multi-step attack involves deceiving guests through a fake Booking.com payment page, resulting in a higher success rate for credit card theft.
Key Takeaways to Hotel Hackers Using Fake Booking.com Pages to Steal Guests’ Credit Cards:
- Cybercriminals employ a multi-step scheme targeting hotels, travel agencies, and booking sites to access customers’ financial information.
- The attack begins with a seemingly innocent reservation query or request, leading to the deployment of stealthy info-stealing malware.
- Hackers leverage direct and trusted communication channels to send phishing messages, impersonate legitimate requests, and trick victims into revealing credit card details.
Sophisticated Info-Stealing Campaign
Security researchers have identified an intricate information-stealing campaign that specifically targets the hospitality industry, including hotels and travel agencies.
This campaign involves the use of advanced social engineering techniques to deliver malware designed to steal sensitive data.
Deceptive Reservation Inquiries
The attack starts innocuously, often with a reservation inquiry or reference to an existing booking.
The cybercriminals establish communication with the hotel and then provide a seemingly valid reason, such as a medical condition or special request, to send important documents via a URL.
Info-Stealing Malware
The provided URL leads to info-stealing malware that operates covertly, collecting critical data like login credentials and financial information.
Targeting Customers Directly
In a more advanced stage of the attack, cybercriminals target the compromised entity’s customers. After deploying the info-stealer on the initial target (the hotel), the attacker gains access to legitimate customer messaging.
Phishing via Trusted Channels
Using the compromised communication channel, cybercriminals send phishing messages, disguising them as authentic requests from the compromised hotel or booking service.
These messages typically request additional credit card verification, employing convincing language and rationale.
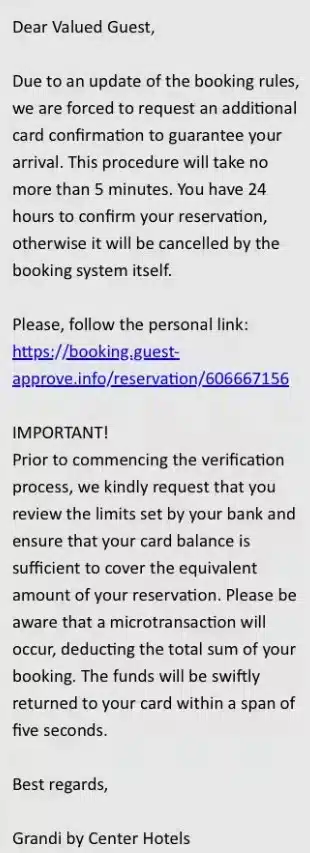
Professional and Legitimate-Looking Messages
The phishing messages are meticulously crafted to appear professional and mimic genuine interactions between hotels and guests, making them difficult to suspect as fraudulent.
Legitimate Communication Channels
Importantly, these messages originate from the booking site’s official communication platform, eliminating suspicion and reinforcing their legitimacy.
Complex JavaScript and Fake Booking.com Page
Victims receive a link for alleged card verification to secure their reservation. Clicking the link triggers an executable encoded in a complex JavaScript base64 script. This script serves to obfuscate browsing environment detection, making analysis challenging.
Sophisticated Anti-Analysis Measures
The attacker has integrated multiple security validation and anti-analysis techniques to ensure that only potential victims progress to the next stage of the scam. This stage presents a fake Booking.com payment page.
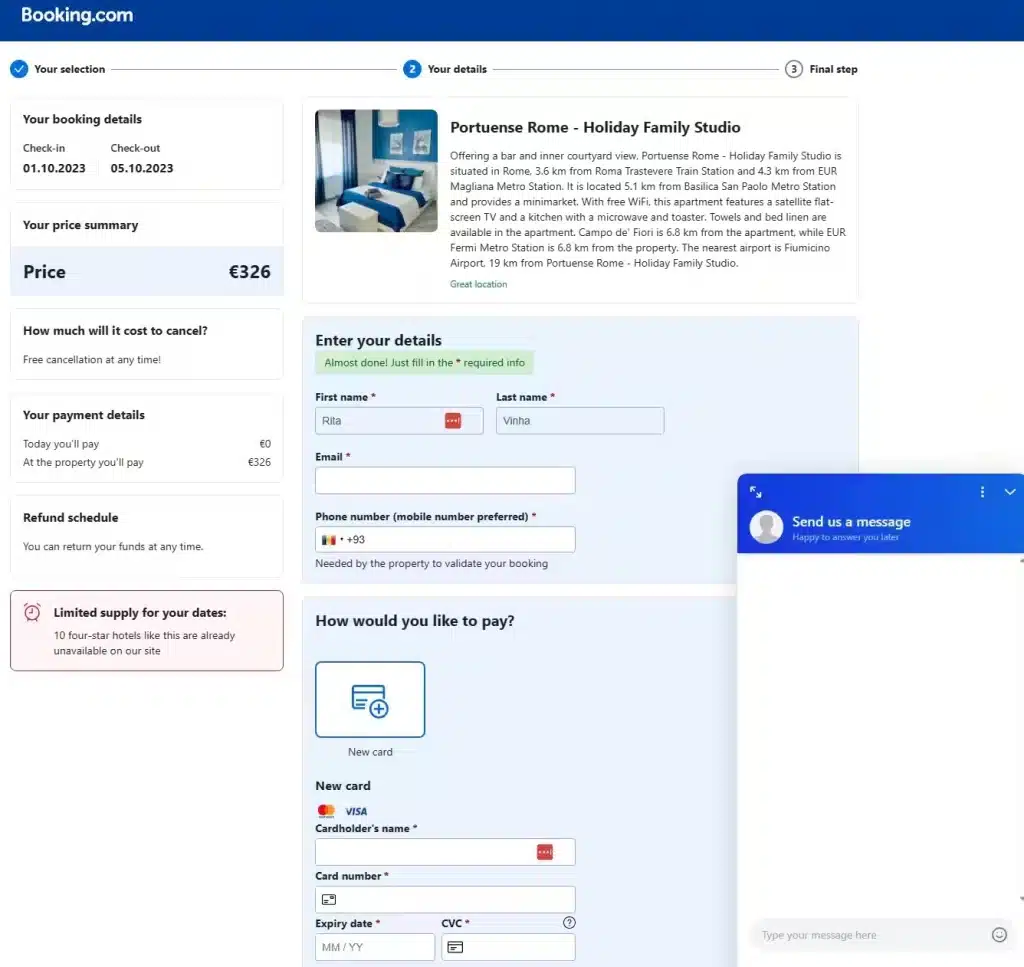
Remain Cautious and Vigilant
Despite the sophistication of this scheme, there are still signs that can indicate a potential scam.
Users should avoid clicking unsolicited links, especially those demanding immediate action, and scrutinize URLs for signs of deception.
Contact Companies Directly
To safeguard against complex phishing campaigns, it’s advisable to contact the company directly using official contact details and seek clarification regarding suspicious messages.
Conclusion
This elaborate cyber-attack reveals the evolving tactics of cybercriminals targeting the hotel and travel industry. Awareness, caution, and direct communication with companies are crucial in protecting against such sophisticated schemes.
About Perception Point and Akamai:
Perception Point and Akamai are prominent names in the cybersecurity sector, specializing in threat detection and internet services, respectively. Their expertise plays a critical role in identifying and addressing cyber threats.





