Table of Contents
Exploited Flaw in WooCommerce Payments Plugin Enables Website Hijacking: Cybercriminals are actively taking advantage of a critical security flaw in the WooCommerce Payments WordPress plugin, leading to a widespread targeted campaign.
The flaw enables attackers to bypass authentication and impersonate users, potentially resulting in a site takeover.
Key Takeaways to Exploited Flaw in WooCommerce Payments Plugin Enables Website Hijacking:
- Threat actors are exploiting a critical security flaw in the WooCommerce Payments WordPress plugin, allowing them to impersonate users and gain control over websites.
- The attacks have reached significant proportions, with millions of attempts observed, affecting a large number of vulnerable sites.
- It is crucial for WooCommerce Payments users to update their plugins to the latest patched version and ensure the security of their websites.
A recently disclosed critical security flaw in the WooCommerce Payments WordPress plugin is being actively exploited by threat actors, leading to a large-scale targeted campaign.
The vulnerability, known as CVE-2023-28121, allows attackers to bypass authentication and assume the identity of arbitrary users, potentially leading to the takeover of affected websites.
Widespread Attacks and Vulnerable Versions
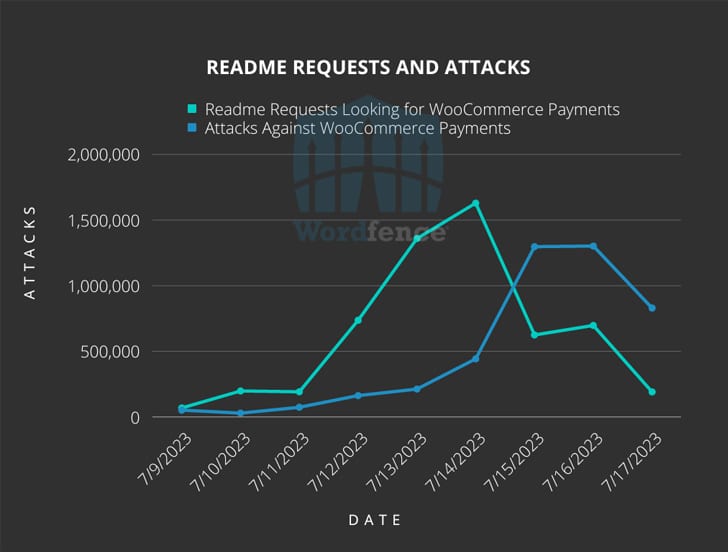
According to Wordfence security researcher Ram Gall, the attacks against the CVE-2023-28121 vulnerability began on July 14, 2023, and continued with a peak of 1.3 million attacks targeting 157,000 sites on July 16, 2023.
The flaw affects versions 4.8.0 through 5.6.1 of the WooCommerce Payments plugin, which is installed on over 600,000 websites. While patches for the vulnerability were released in March 2023, it is crucial for website owners to ensure they are using the latest patched version of the plugin.
Exploitation Method and Malicious Payloads
The attacks exploit the vulnerability by utilizing the HTTP request header “X-Wcpay-Platform-Checkout-User: 1.” This header causes vulnerable sites to treat additional payloads as if they were coming from an administrative user.
In the current campaign, attackers are leveraging this loophole to deploy the WP Console plugin, which allows an attacker to execute malicious code and install a file uploader, providing persistence and a backdoor into compromised websites.
Rapid7 Discovers Exploitation of Adobe ColdFusion Flaws
In addition to the WooCommerce Payments plugin flaw, Rapid7 has reported active exploitation of vulnerabilities in Adobe ColdFusion.
Starting from July 13, 2023, threat actors have been using the vulnerabilities to deploy web shells on compromised endpoints. The primary flaw, CVE-2023-29298, is an access control bypass vulnerability affecting ColdFusion 2023 and earlier versions.
It allows attackers to access administration endpoints by inserting an unexpected additional forward slash character in the requested URL.
Incomplete Patch and Necessary Updates
Rapid7 has cautioned that the fix for CVE-2023-29298 in Adobe ColdFusion is incomplete and can be easily bypassed. However, updating to the latest version of Adobe ColdFusion is still recommended, as the patches implemented to address CVE-2023-38203, a related deserialization flaw, break the exploit chain.
Conclusion
The exploitation of critical security flaws in the WooCommerce Payments WordPress plugin and Adobe ColdFusion underscores the importance of prompt updates and vigilant security measures.
Users should ensure they are running the latest patched versions of affected software to protect their websites from potential hijacking and other malicious activities.
Staying informed about emerging vulnerabilities and following recommended security practices are essential steps in maintaining a secure online presence.





